
Google Drive was launched on April 24, 2012, over a decade ago. Since then, millions of organizations across the globe have put their trust and stored corporate data in Google Drive. In parallel, the Cloud Access Security Broker (CASB) security product category was formed to protect data stored in SaaS applications, such as Google Drive, from insider threats, malicious activity, and data overexposures. This blog post outlines why DoControl is the world’s leading CASB for Google Drive specifically, but also for other top SaaS applications.
To protect your Google Drive data, you first need to understand how much data you have, who owns it, across what business unit, how is it exposed, etc. DoControl uses a robust API integration to pull all metadata representing your Google Drive instance data and break it down in a quantified manner. Discovery takes 12-24 hours and scales into the dozens of terabytes.
Upon completion of data discovery, DoControl clearly surfaces your Google Drive attack surface, showing data overexposure, identity permission overexposure, and dozen other threat models. This entire process is done with no initial configurations or complex settings whatsoever.
In addition, DoControl subscribes to Google Drive’s webhook activity events so that whenever end-users and/or OAuth apps consume Google Drive from mobile, desktop, web, or API, Google pushes the relevant event information to DoControl in near real-time. This enables DoControl to clearly monitor for ongoing and suspicious user behavior across all Google Drive internal users, external collaborators, and 3rd party OAuth applications.
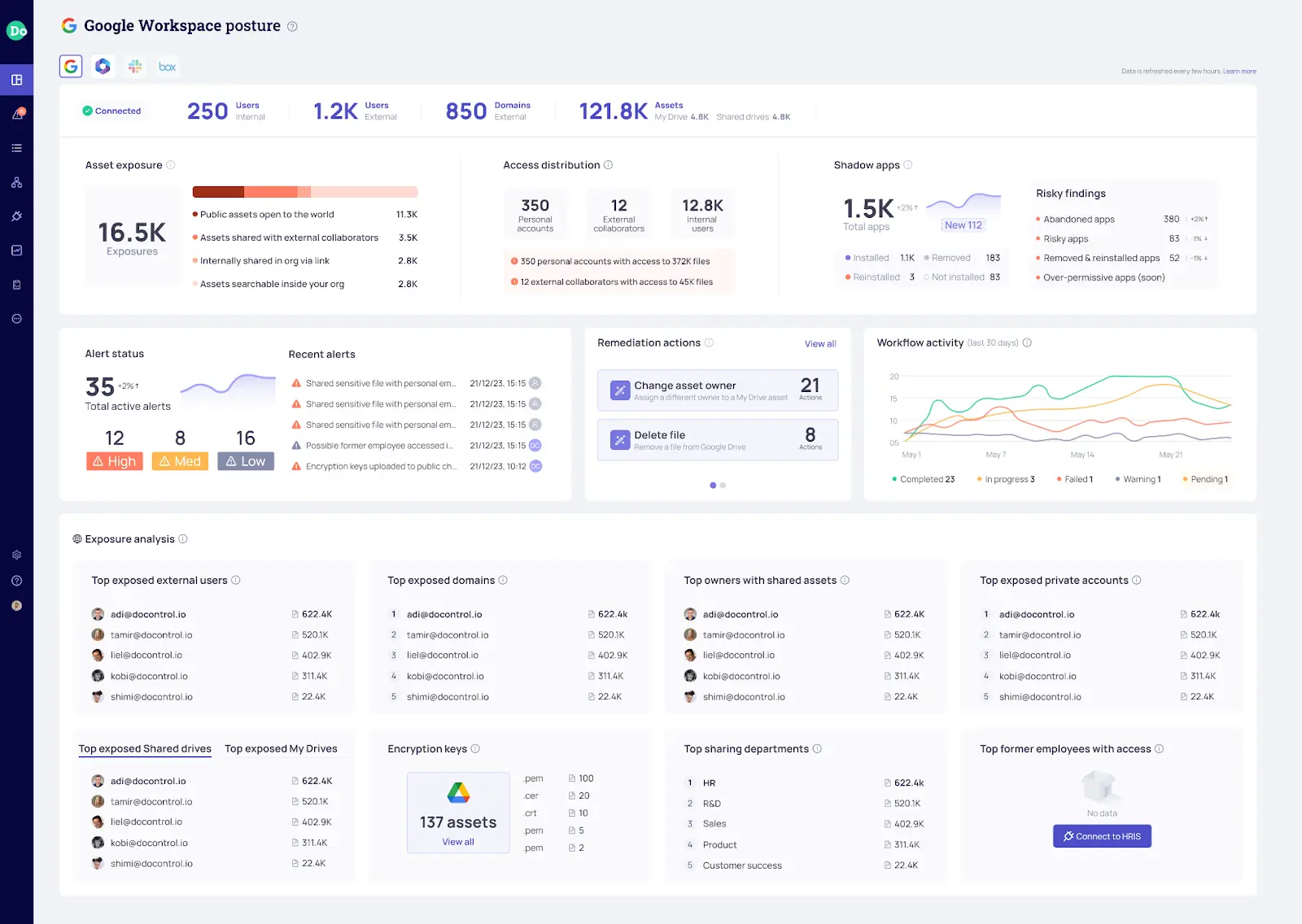
Google Drive customers are what we call “Google Shop” customers - leveraging a combination of Google and non-Google products as part of their IT stack. This means that critical business context is stored outside of Google Workspace, such as HR information, Identity/Group, etc. Therefore, DoControl is integrated with HRIS products (Workday, BambooHR, Hibob) and Identity Providers (Okta, Azure AD) to pull critical business data sources around employment status, department/org hierarchy, group membership, and more.
These signals help DoControl aggregate its data layer by contextual organizational structure and across Identity Configurations from your IdP. From there, DoControl enriches its data layer across both Data Inventory and Activity Events to surface a more accurate risk profile.
Users can filter their Google Drive environment according to business context from HRIS and IDP, and then correlate with Google Drive’s common signals, such as sharing status or modified date. This helps quantify security investigations, data access reviews, and remediation planning.

The combination of data inventory showing a clear attack surface, and business context from HRIS/IDP enables DoControl to alert on suspicious activity with specific business risks in place as well as common industry risk factors. This results in high accuracy threat detections providing full context to potential incidents as well as reliable remediation paths.
Users can fine-tune alerting sensitivity and keywords to retrieve more or less relevant alerts as per business requirements. Alerts are connected to workflows to deploy granular and consistent remediation playbooks involving no meetings/tickets.

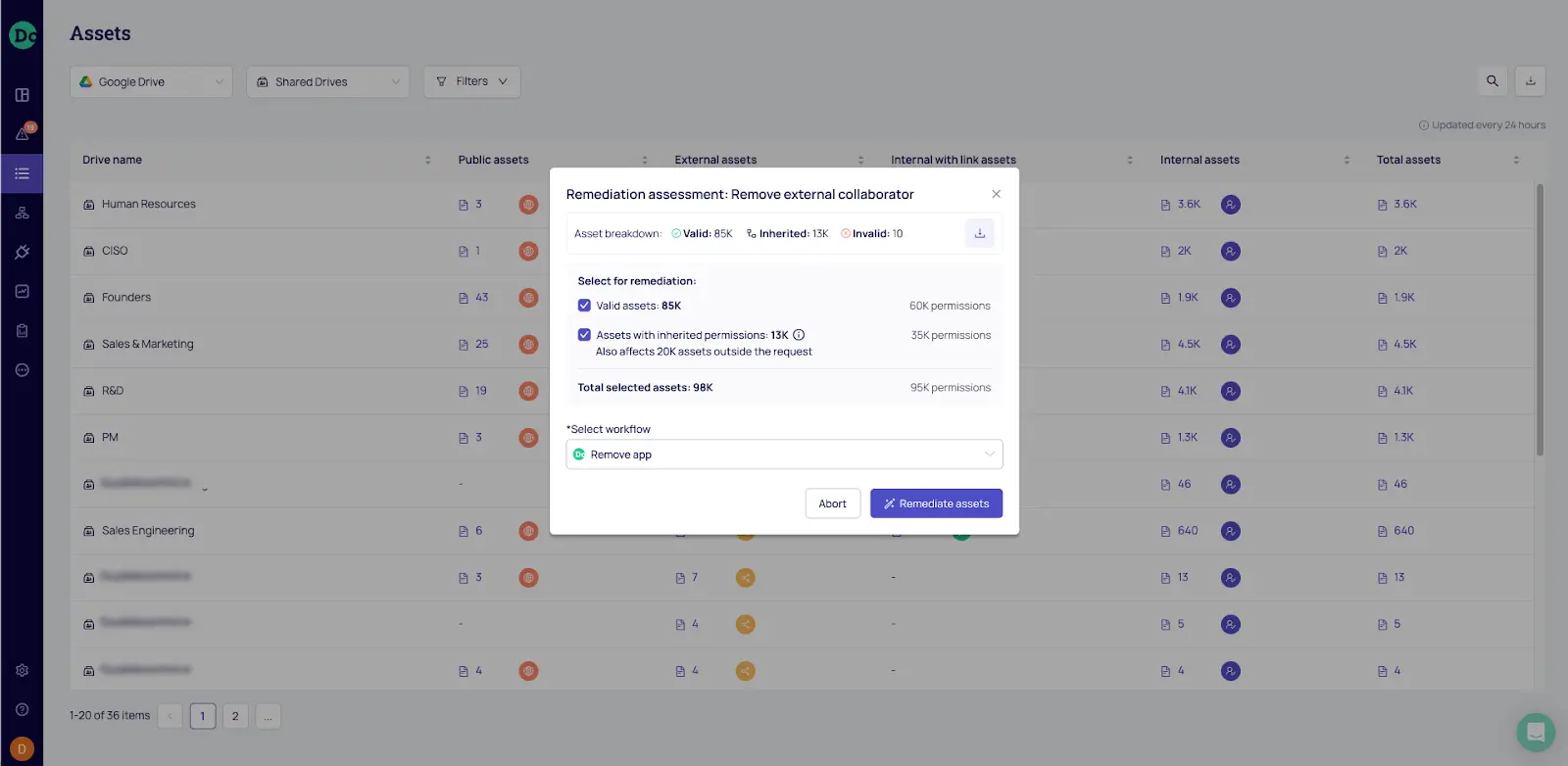
In most cases, initial data discovery showcases a very large attack surface based on years of data exposures that were not remediated. For this scenario, DoControl offers a patented Bulk Remediation capability that reduces sharing permissions in the millions through a few clicks.
Users filter the data inventory based on specific data sets, business units, 3rd party collaborators, etc. and then hit the bulk remediation action. From there, DoControl provides a data assessment on the volume of permissions to be removed, potential impact, etc. Submitting the bulk remediation results in a fully automated process that works behind the scenes to remediate millions of sharing permissions.
With so many user interactions, data collaborations, and potential suspicious activity, DoControl offers fully automated workflows that go into the deepest level of granularity and remediation options. Users can trigger workflows based on ANY Google Drive activity event, condition the workflow based on ANY of that event’s metadata, enrich with HRIS/IDP business context, perform all kinds of remediation paths (remove share, delete file, run approvals, etc), and send the information directly to the customer’s SIEM/SOAR or any other SOC platform.

Most Google customers are also Slack customers, in which end-users live and work daily. With DoControl, security teams can get end-users’ business context on their Google Drive activity events through customized, granular, and intuitive Slack Bot messages. This enables end-users to input their perspective and help security teams dismiss or validate potential risk, without extra meetings nor tickets in place.

All in all, DoControl provides a broad and deep solution for Google Drive customers who want to benefit from world-class data security over their corporate data. From data discovery, to understanding risks, to remediation and automation - DoControl is built for Google Drive’s complexity, scale, and modern consumption patterns.
.webp)
Research-based benchmarks to assess risk across critical threat model


Discover why sensitive data discovery tools often trigger false alarms, causing frustration for InfoSec teams. Learn why this happens and how to find tools for accurate detections.


Learn about the three primary types of Zoom vulnerabilities: in-meeting, data storage, and system access risks. Safeguard your organization effectively against these threats.


SaaS solutions are integral for workflows, granting anytime access to critical data. Yet, without robust SaaS Access Control Management, businesses face significant security risks.
