
Customers Rank DoControl as #1 in SaaS Data Security
DoControl has revolutionized our SaaS security strategy, delivering the visibility, precise risk detection, and scalable remediation necessary to protect our data at scale. End users praise the seamless experience, and our security team values the simplicity of deployment and ongoing management. For any organization running SaaS - especially Google Workspace - DoControl is essential.

Market Problem
The Business Collaboration Shift
in the AI Era
How modern organizations share data in an AI-accelerated workplace
- Cloud-native platforms (Google Workspace, M365) power modern, AI-enhanced collaboration
- Real-time co-editing and AI agents accelerate productivity
- External sharing is more frequent, and increasingly difficult to monitor without intelligent oversight
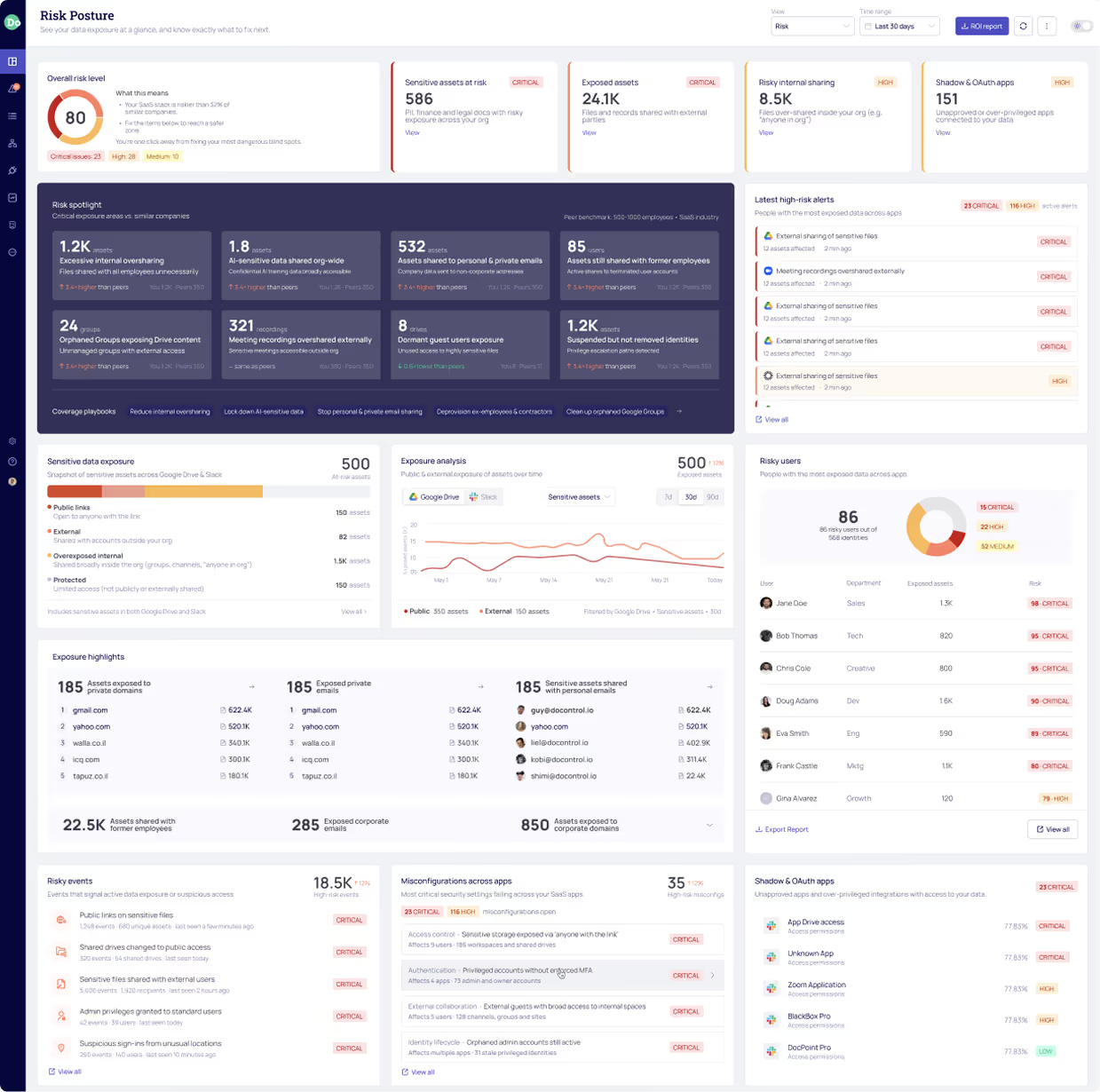
The New Risk Landscape
Increased collaboration exposure in an AI-driven ecosystem
- Data flows continuously across internal and external boundaries
- Manual controls lack the intelligence to track who is sharing what, with whom, and why - and if it's a human or an AI agent (NHI)
- Sensitive data leakage is easier, faster, and harder to detect
- Example risks: financial exposure, IP theft, unauthorized external access
Why Legacy DLP Can’t Keep Up in AI-Powered SaaS Environments
Traditional controls weren’t designed for AI-accelerated collaboration
- Rigid “allow/block” models rely solely on static content scanning
- Slow, agent-based detection misses time-sensitive events
- Detection models lack contextual and AI-powered behavioral insight
- Creates operational friction, user frustration, and business disruption
The Missing Piece: Intelligent Identity & User Context
Content alone cannot determine risk, modern SaaS ecosystems demand AI-powered contextual insight
- The same data can be risky or safe depending on: who is sharing, who is receiving, what their role is, and more.
- Example 1: CFO → Deloitte (a legitimate share, wrongly blocked by DLP)
- Example 2: Departing employee → personal email (high-risk data exfiltration action, missed by DLP)
- Example 3: AI Agent (NHI) → Bulk data access & external sharing (HIGH risk, a non-human identity accessing sensitive files outside its usual pattern, missed by DLP)


Why

AI-Driven Contextual
Data Protection
Former employees with lingering access, sharing data to private email domains, rogue AI agents accessing sensitive files, & more.


Intelligent Identity
& Behavioral Risk Protection
Former employees accessing confidential data, about to-leave users downloading files, AI agents accessing risky data, & more.


Scalable AI-Powered Historical & Ongoing Remediation
Remediate exposure across assets, apps, & identities - enforcing context-aware protections to eliminate past, present, & future exposure.


Automated Policies & Business Process Alignment
Leverage AI-powered workflows to trigger automated remediation, user engagement, and policy enforcement, all in real time.

The

Solution
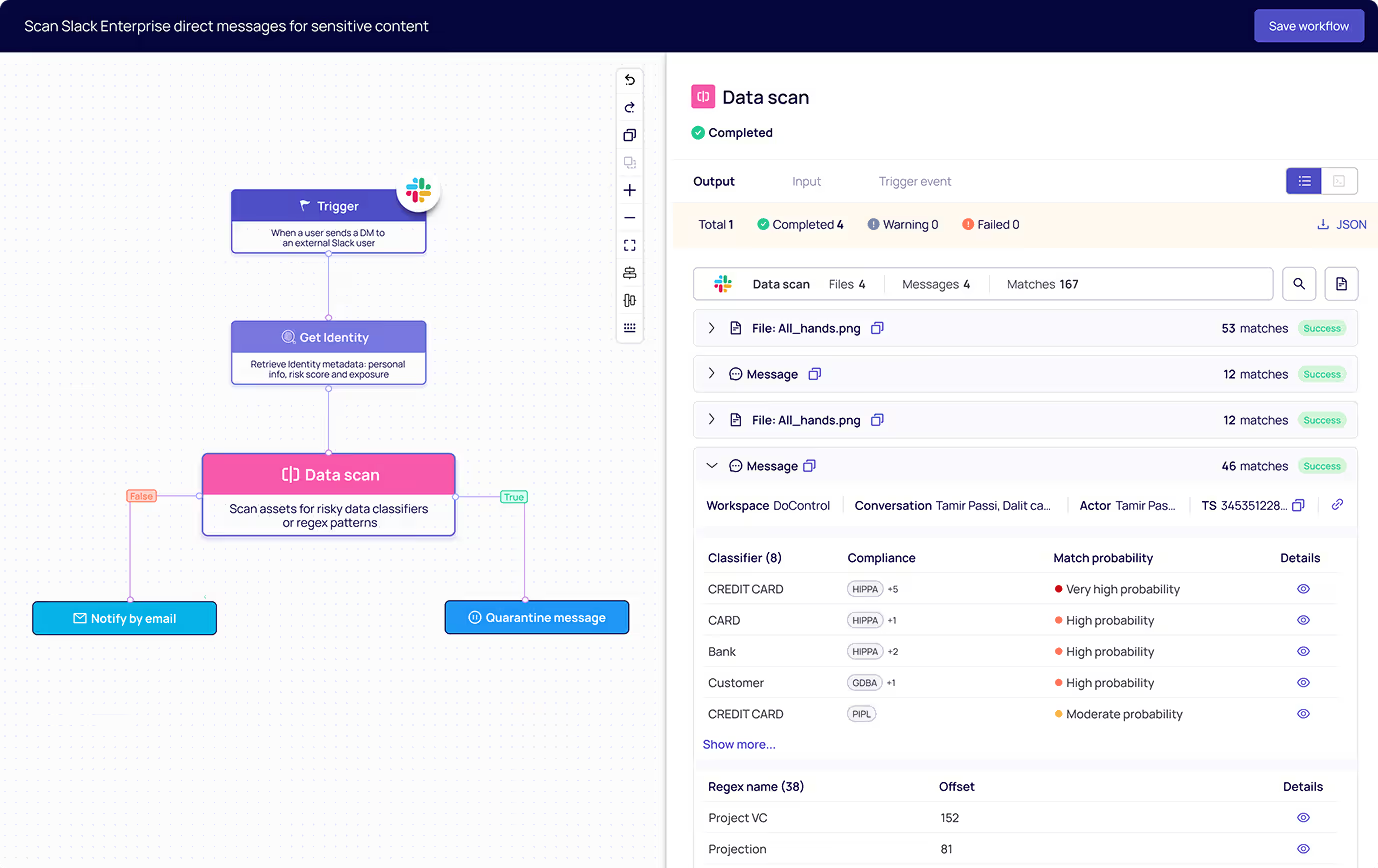
Remediate risk in real time using content, identity, and user context - without blocking legitimate business activity.
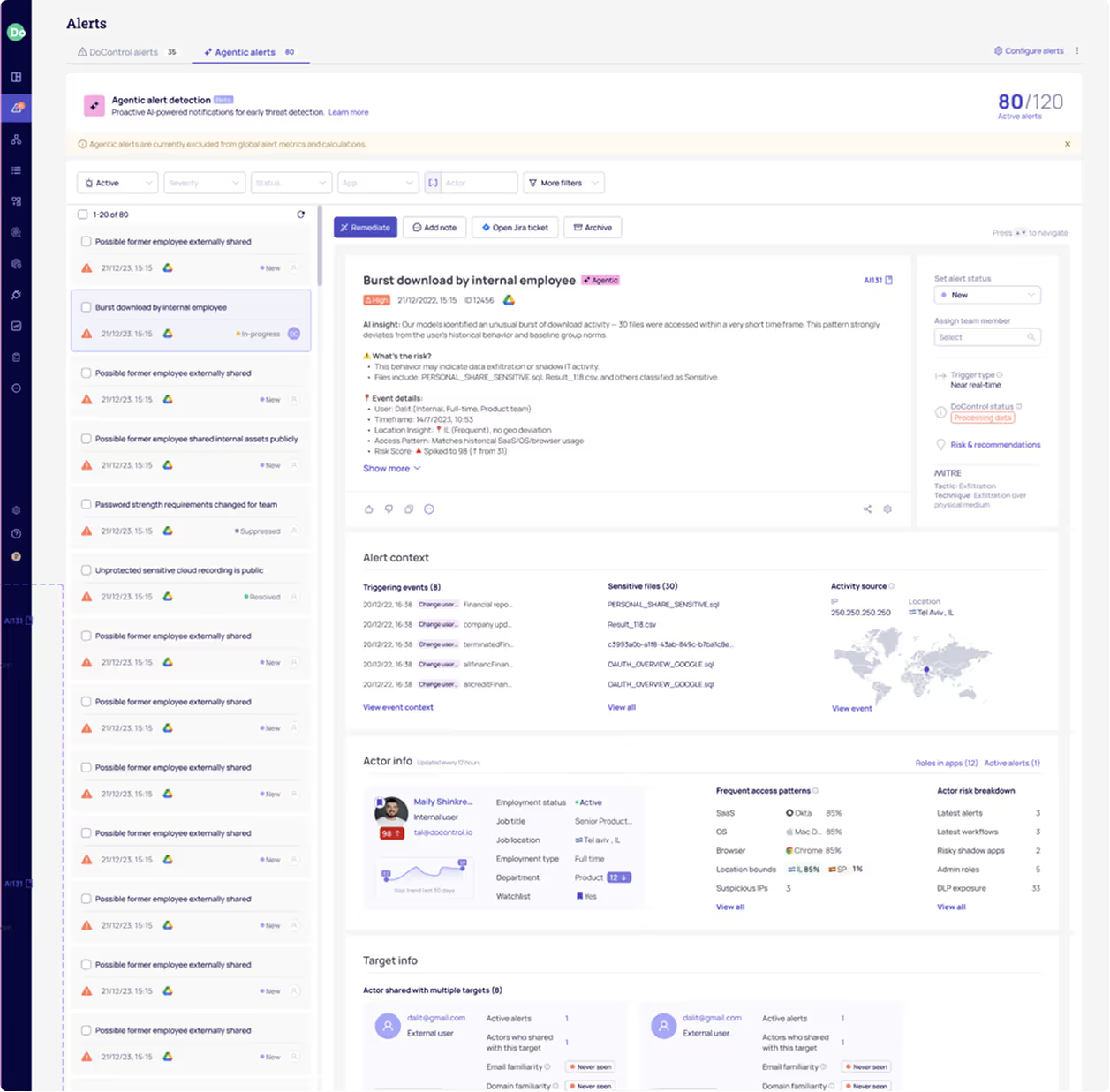
Baseline user behaviour, benchmark against teams, and identify and remediate anomalous actions.
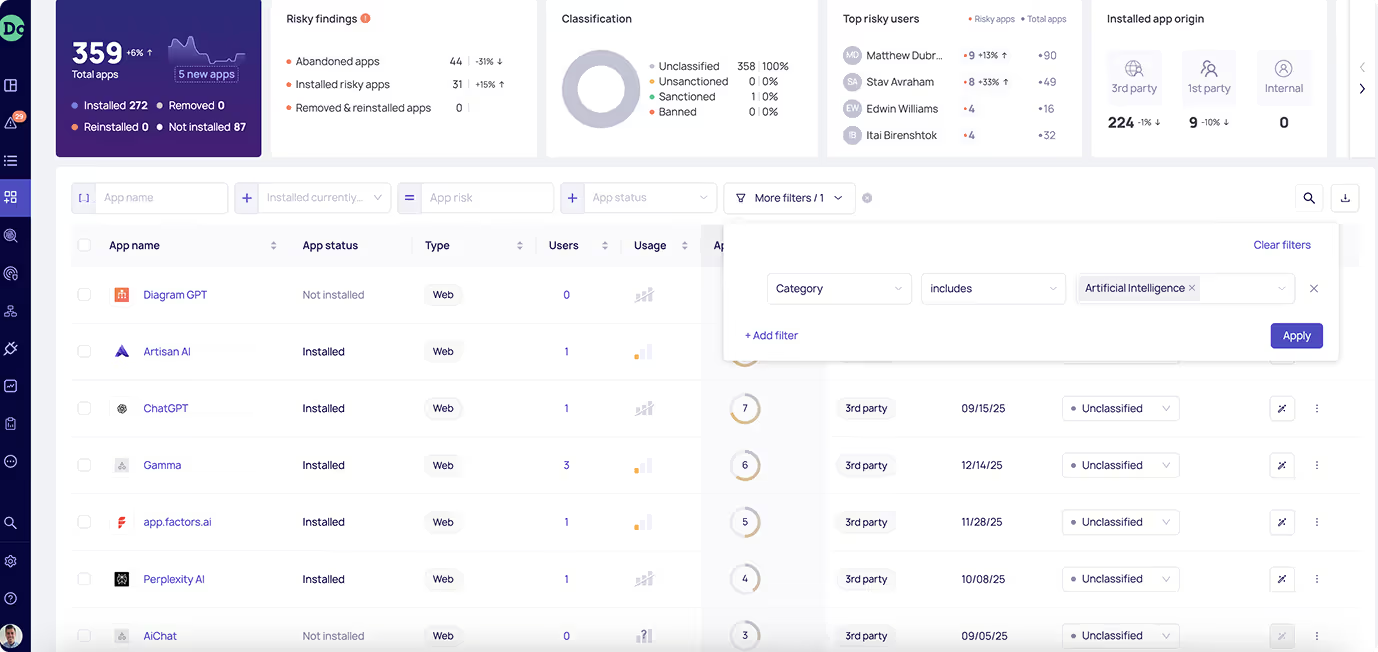
Inventory, risk score, and remediate every risky app - human or non-human - within your environment.
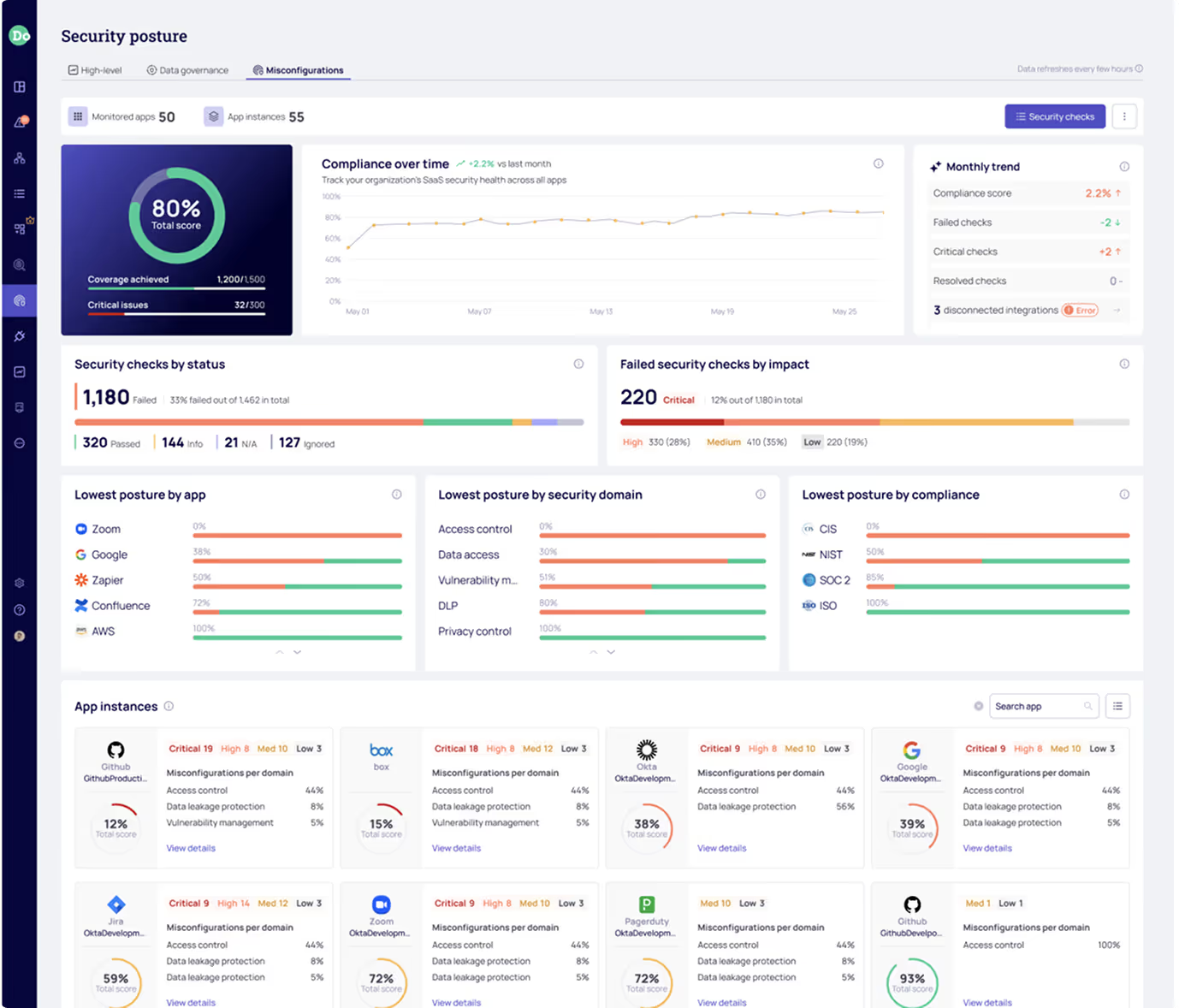
Ensure every SaaS application in your environment is properly configured to meet compliance frameworks.
Let’s hear what our customers have to say
Stop Flying Blind
Get your free SaaS risk assesment and discover the blind spots in your data security posture.
No Commitment required.
Great!
Please make sure to pick a date for an intro call.
We've opened the calendar in a new tab
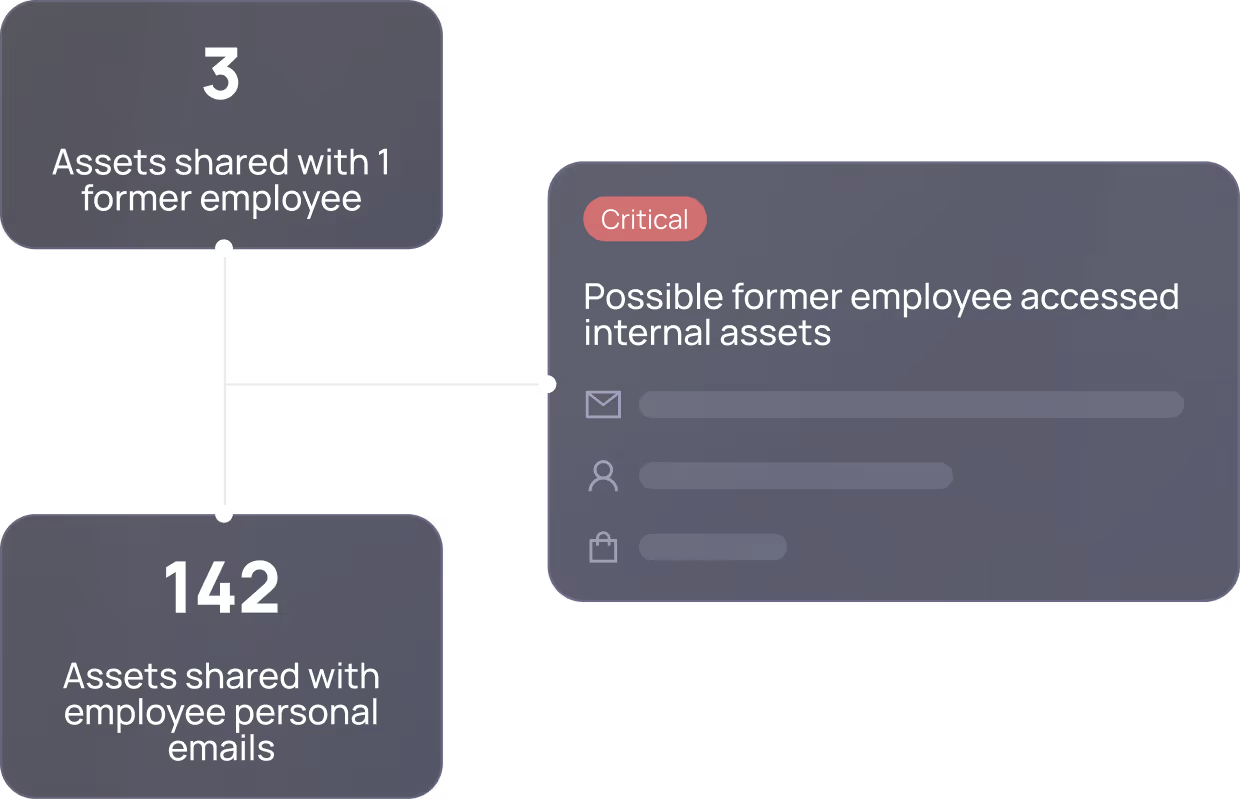
Reopen CalendarFormer Employees w/ Access
Board Files Shared Publicly
Departing Employing Downloading Sensitive Files
















.png)









.png)