
The rise of remote work has revolutionized how employees collaborate, but it has also introduced significant security risks. As organizations adapt to flexible work environments, the challenge of protecting sensitive information, devices, and networks becomes more complex – especially when remote workers are accessing cloud-based systems from personal or unmanaged devices.
Traditional security measures designed for office-based setups are no longer enough, and are becoming increasingly irrelevant. To protect today’s distributed workforce, companies must implement modern security solutions that provide visibility, control, and automation across all endpoints and access points – without compromising productivity.
In this article, we’ll explore the risks unique to remote work environments, why perimeter-based security models fall short, and how a Zero Trust approach combined with cloud-native security tools can help organizations secure their remote workforce effectively.
Understanding the Security Risks of Remote Work
Remote work introduces a host of cybersecurity challenges that IT teams must navigate carefully. The rapid shift to remote work post-covid has significantly expanded the SaaS attack surface.
Unlike controlled office environments, today's remote workers depend heavily on cloud-based collaboration tools, often without proper oversight or governance. This introduces complex challenges for security teams trying to protect corporate data, enforce compliance, and mitigate insider and external threats.
Modern remote work environments are booming with risks – not just at the endpoint or network level, but within the SaaS layer itself, where most business-critical data now resides. Think Google Workspace, Slack, Microsoft 365, etc…
Key SaaS Security Risks in Remote Work:
- Shadow apps and unsanctioned services: Employees often connect unauthorized third-party shadow apps via OAuth to platforms like Google Workspace or Microsoft 365, creating unauthorized data flows and violating compliance policies. Without visibility into these apps being integrated, IT and security teams are in the dark as to how data is being used – or misused – by their employees .
- Over-permissive file sharing: Remote employees frequently overshare docs or files via SaaS platforms, exposing internal data externally through public links or excessive sharing permissions. These misconfigurations are a leading cause of data breaches and data exfiltration.
- Unmanaged identities and excessive access: As remote teams grow, so does the number of users, collaborators, and third-party accounts with access to sensitive content and company data. Without proper data access governance, it’s nearly impossible to enforce the principle of least privilege or identify risky access patterns.
- Identity-based threats (ITDR): Compromised accounts, insider threats, and abnormal user behavior are increasingly difficult to detect when users are distributed and working from home. Remote access from unknown devices, locations, or IP addresses can go unnoticed and fly under the radar without contextual monitoring and automated controls in place.
- Compliance gaps: With data dispersed across multiple SaaS services and shared from unmonitored devices, maintaining compliance with frameworks like SOC 2, HIPAA, or ISO 27001 becomes a challenge – especially when security policies aren’t automated or enforced consistently.
Organizations must take these risks seriously to maintain a high level of security while supporting the flexibility of remote work.
Why Legacy Security Fails in a SaaS-Centric, Remote World:
Legacy security architectures were never designed for the cloud-first, remote work reality we operate in today. They rely heavily on perimeter-based controls and agent-based solutions – approaches that fall apart when employees are working from personal laptops, mobile phones, or devices outside of IT’s control.
- Zero visibility into SaaS data exposure: Once files are shared or permissions are granted in Google Drive, Slack, or Microsoft 365, perimeter tools can’t tell you who has access, whether it’s appropriate, or if that access has been misused.
- No detection of shadow apps: Firewalls can’t monitor OAuth connections or unsanctioned third-party apps that users install to “get work done.” These integrations often bypass IT completely – yet they’re deeply connected to business-critical cloud data. Even worse, in 2025, the risks of AI shadow apps bring on an entirely new attack surface that didn’t exist previously.
- Lack of identity context: Perimeter-based tools are blind to identity based threats – like former employees retaining access, compromised accounts engaging in suspicious behavior, or contractors with lingering excessive permissions.
- Agent-based blind spots for BYOD: Many remote employees use personal devices that are not managed by IT. Agent-based solutions – which require software to be installed on every endpoint – don’t work in these cases. BYOD environments leave major visibility and control gaps that legacy tools simply can’t cover, making them ineffective at enforcing consistent security policies or detecting threats across the full remote workforce.
- Inability to automate SaaS controls: Legacy solutions don’t have the power to remediate exposure at scale. They can’t revoke a public link, quarantine a file, or enforce file-sharing policies within your SaaS stack.
- End-user friction and workarounds: Access issues often lead remote workers to bypass security protocols altogether, further hurting the organization’s security posture. Employees will usually do what's most convenient for them, and won’t take the security first approach if it will hinder their day-to-day business ops.
In short, agent-based and perimeter-based security solutions can't extend into the SaaS layer – where today’s work, data sharing, and collaboration happen. They weren’t built for a remote-first, BYOD-heavy, cloud-native reality.
To truly protect remote workers, organizations need cloud-native, identity-aware solutions that operate directly within the platforms their employees use – without relying on endpoint agents or perimeter assumptions.
Essential Components of a Modern Remote Work Security Strategy
To effectively secure remote work, organizations need a modern, layered security strategy. This means shifting focus from infrastructure-centric tools to data, identity, and automation-driven controls.
Here are the critical components:
1. Data Access Governance
Start with visibility: know who has access to what across all connected SaaS applications. Automatically remove stale permissions, over-privileged users, and unnecessary third-party integrations that increase risk.
2. Zero Trust Architecture
Adopt a Zero Trust framework where nothing is inherently trusted, especially in decentralized environments. Every user, device, and access attempt should be validated based on role, behavior, and data sensitivity. SaaS environments require policy enforcement within the application, not just at the perimeter.
3. Shadow App Discovery and Control
Remote employees frequently connect third-party apps to SaaS platforms without IT approval. These shadow integrations can exfiltrate data or open security gaps.
4. SaaS-Native Data Loss Prevention (DLP)
Traditional DLP doesn’t apply well in the cloud. Organizations need SaaS-aware DLP that can enforce file sharing policies, flag risky behaviors, and stop data breaches before they happen – without disrupting user productivity.
5. Identity Threat Detection & Response (ITDR)
As remote workers use multiple ‘identities’ (log-ins, credentials, etc.) and collaborate across domains, detecting identity-based threats becomes critical. Look for abnormal activity, such as off-hours file downloads, contractors accessing sensitive data, or compromised accounts behaving unusually.
6. Automated Security Policies
Create and enforce contextual, low-friction security policies that operate in real time. For example, block public sharing of files containing PII or automatically quarantine sensitive documents shared externally. Automation ensures consistency and scale without overburdening security teams.
DoControl: Automating SaaS Security for the Remote-First Enterprise
Securing a remote workforce in today’s SaaS-driven world demands more than traditional tools or manual processes. With thousands of users, files, apps, and sharing events in motion daily, security teams need intelligent, scalable automation to stay ahead of risk.
DoControl was purpose-built to meet this challenge – providing a unified platform for data access governance, DLP, shadow app control, and identity threat detection and response (ITDR).
Delivered through our SaaS Security Posture Management (SSPM) solution, DoControl empowers security teams to proactively manage data exposure across the modern SaaS stack. Our platform gives you COMPLETE visibility into every single event, user, and action happening in your organization.
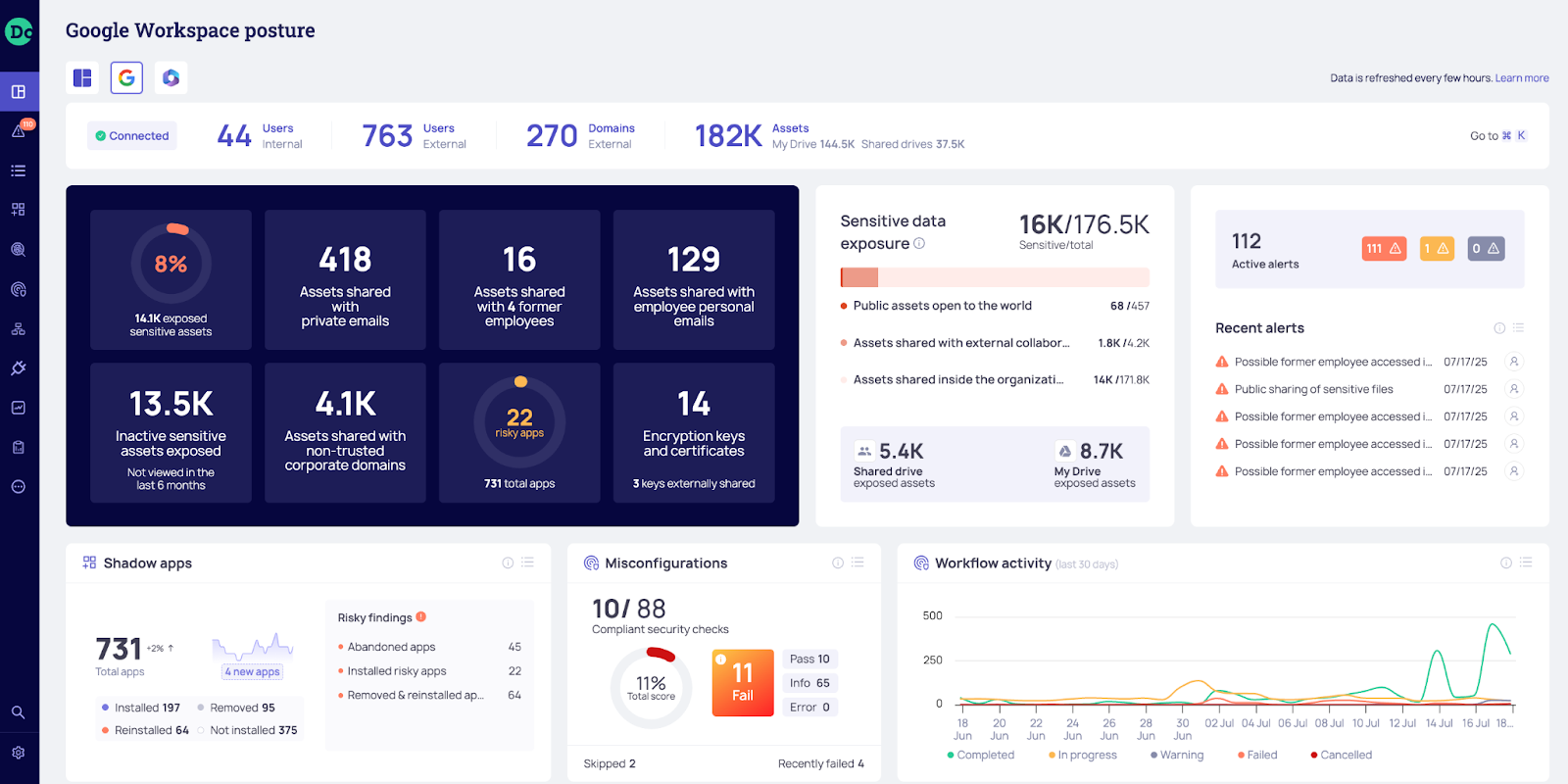
Why DoControl Is Ideal for Securing Remote Work:
- No-code, automated policy workflows: Create flexible, contextual, workflows that engage end-users and enforce security policies in real time – revoking excessive file access, blocking unsanctioned third-party apps, quarantining risky shares, and detecting abnormal behavior. All without writing code or slowing down operations!
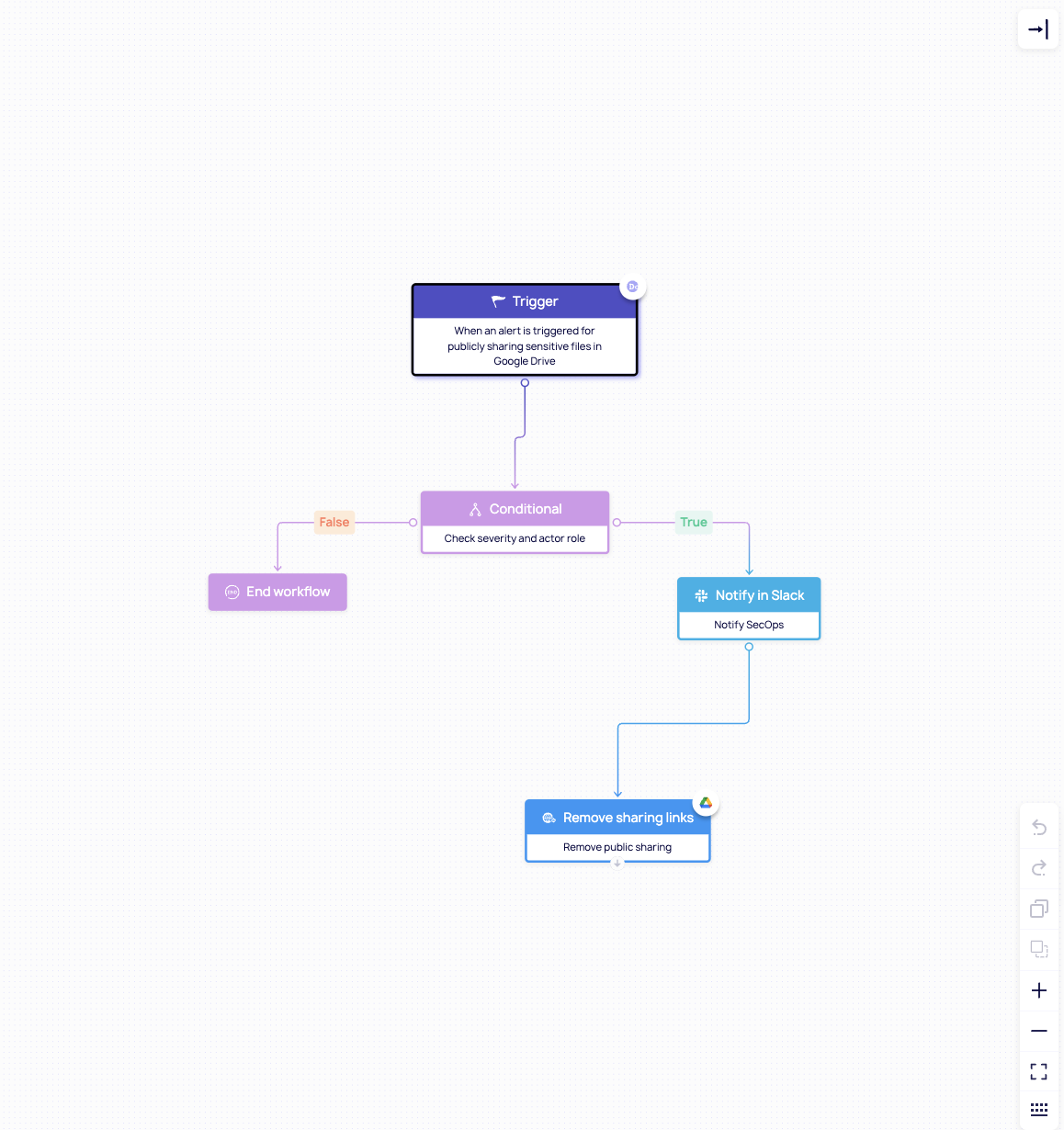
- SaaS-native visibility
Gain full visibility into how files are shared, who has access to what, and where sensitive data lives across platforms like Google Workspace, Microsoft 365, Slack, Box, and more. - Automated enforcement at scale
Eliminate manual reviews and ensure consistent data protection across every user, device, and file. DoControl’s automation adapts dynamically to user roles, sharing activity, third-party app connectivity, and compliance requirements.
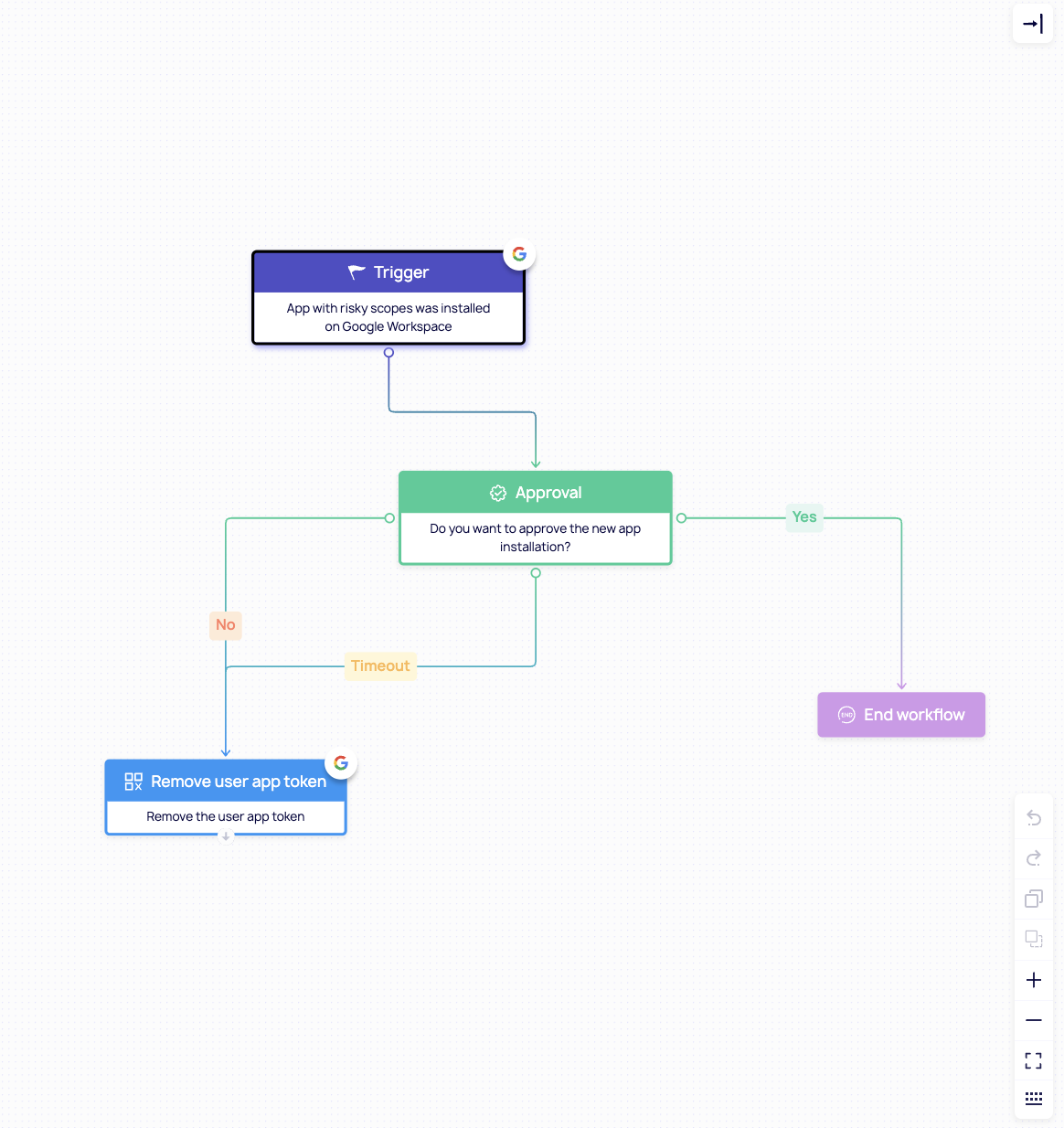
- Real-time threat response
Respond instantly to risky behaviors – like a public link to sensitive content or an ex-employee retaining access – before a breach can occur. - Dynamic access management
Automatically adjust permissions as employees onboard, shift roles, or leave the company – ensuring that nobody in the organization has access to sensitive company when they shouldn’t.
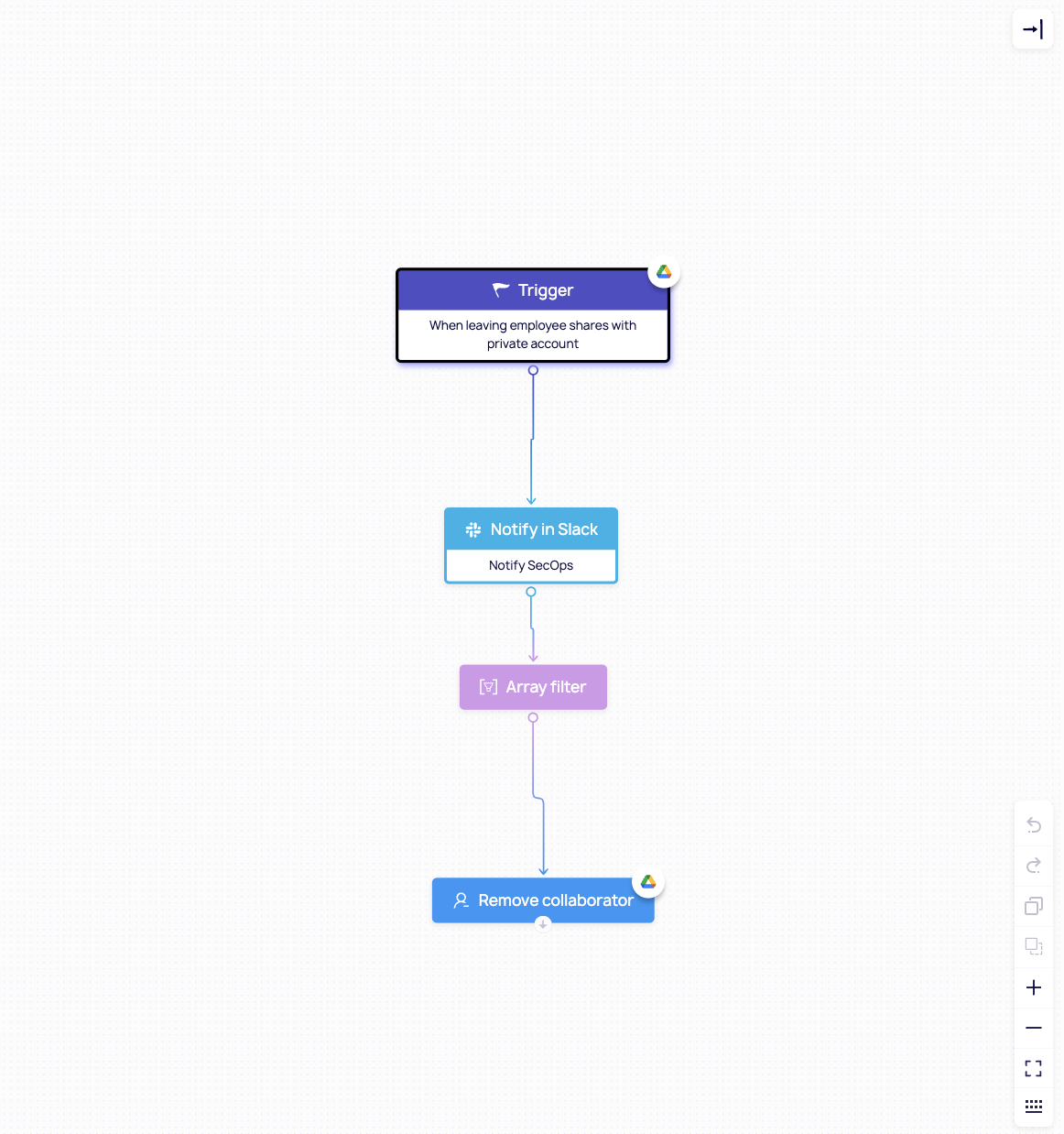
- Frictionless collaboration experience
Enforce strong security controls without disrupting workflows. With DoControl operating in the background, remote employees stay productive while your organization stays protected.
By automating SaaS security at the file, user, and integration level, DoControl helps modern enterprises embrace remote work confidently – reducing risk, streamlining operations, and strengthening their security posture at scale!
Summary
With DoControl, organizations can modernize their remote work security approach by automating protection at the point of risk: the SaaS layer. The result is stronger data security, better visibility, faster response times, and a scalable path to long-term resilience in a remote-first world.
As the line between office and home continues to blur, remote work security must evolve to meet the demands of today’s distributed workforce. Traditional security measures built around the corporate network can’t adequately protect remote workers, their devices, or the critical information they access.
DoControl delivers the tools, visibility, and automation needed to support secure, productive remote working at scale. Whether you're facing the challenges of shadow apps, public sharing, or identity risks, DoControl helps you achieve a higher level of security – without slowing down business productivity.
Want to Learn More?
See a demo - click here
Get a FREE Google Workspace Risk Assessment - click here
See our product in action - click here



