.png)
What's the tea in cybersecurity this week?
A women's dating safety app just did the exact opposite of what it intended to do: put women in danger.
Tea is a viral, up-and-coming dating app that was the top rated app on Apple Charts last week. The app helps women identify potential “red-flag” matches, verify if a date is safe, enables background checks and criminal record checks on men, allows women to warn other women about potential abusers, and more.
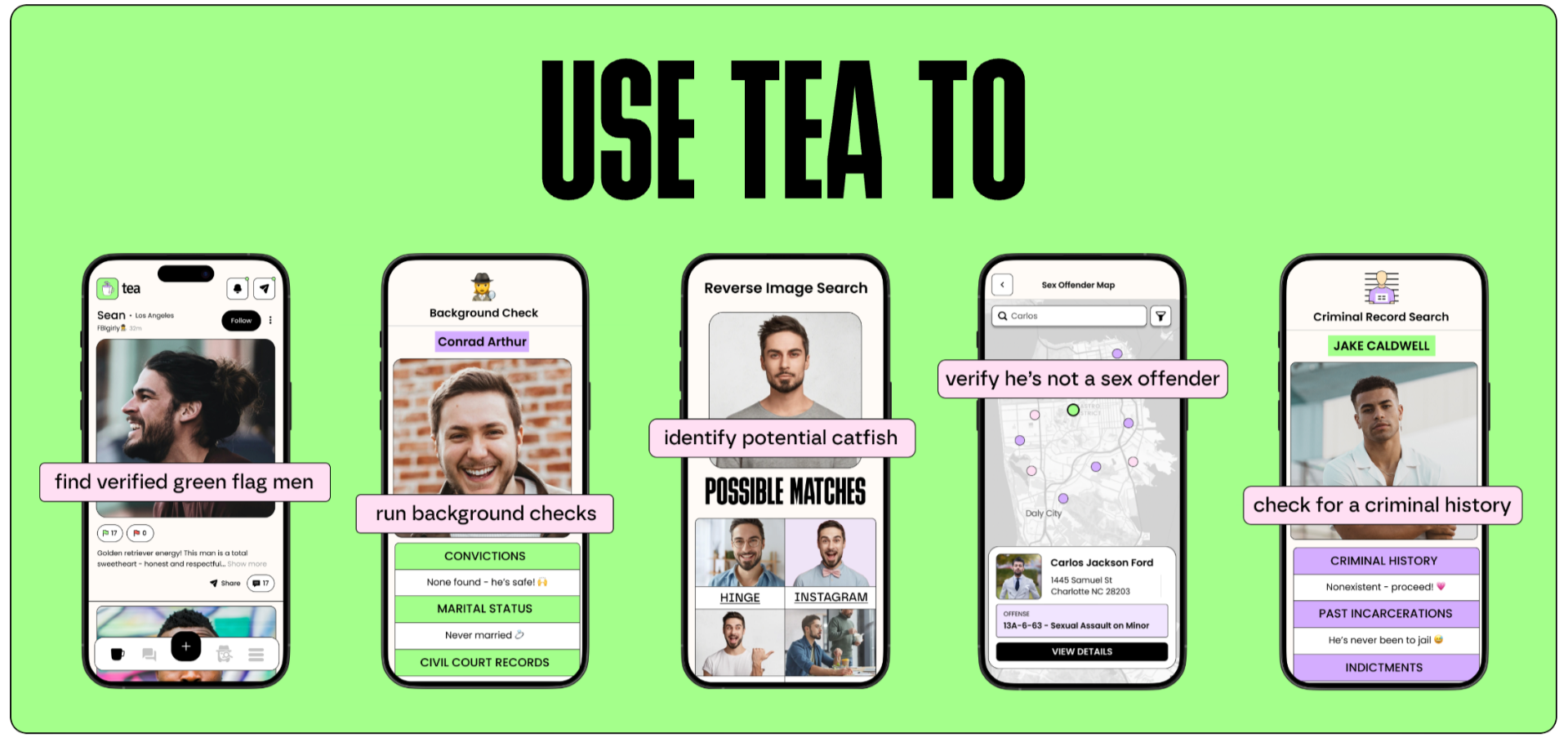
This past week, the app experienced a MAJOR data breach, exposing the very users it was designed to protect.
What Happened in the Tea App Breach?
The breach primarily impacted female Tea users who joined before February 2024, before the app migrated to a more secure infrastructure.
Users who submitted verification selfies and IDs were the most exposed, along with those who posted photos or used the in-app messaging feature. Here's what was leaked:
- 72,000 images were leaked, including:
- Government-issued IDs submitted at sign-up to verify identity
- Verification photos like selfies and profile photos users
- Photos posted by users and shared on the app itself (pictures of from posts and private DMs
- 1.1 million private messages:
- These messages were later discovered, discussing sensitive topics like relationships, other women sharing advice and horror stories, dating safety precautions and tips, and even health concerns.
It goes without saying that all of this leaked information puts these women at SERIOUS risk. For many women, the breach isn’t just about data loss – it’s about real-world safety. ID photos and sensitive conversations could be misused for:
- Identity theft or fraud
- Doxxing or stalking
- Harassment or intimidation online and offline
Many of these women live alone in bigger cities, where now their personal information is in the wrong hands.
How Did The Tea Breach Even Happen?
A user of the platform 4Chan – a notoriously anonymous imageboard website where users can post text and images – posted a public link on Friday (7/25) morning, allegedly allowing people to download the database of stolen images, and files containing victims’ ID photos and selfies.
This data that was exposed – dating as far back as 2023 – was posted to 4chan after the attackers discovered a publicly accessible Firebase storage bucket used by Tea’s Android app.
Tea confirmed the breach to be true, and immediately engaged cybersecurity experts while notifying affected users. However, the damage was already done: private data meant to protect women was now in the wrong hands.
The breach occurred because Tea’s cloud storage was misconfigured, leaving a sensitive Firebase storage bucket publicly accessible on the internet.
What is a Firebase Storage Bucket?
Firebase is a Google cloud platform often used by mobile apps to store things like photos, messages, and user verification data. A “bucket” is essentially a cloud folder where the app’s files live. If that folder isn’t properly secured, anyone who knows the URL can access it – which is exactly what happened to Tea.
When apps scale quickly and handle sensitive personal data like IDs, selfies, and private messages, this creates a SaaS security challenge. Misconfigurations or human error can leave massive amounts of personal data exposed without anyone realizing it until it’s too late.
In this specific case, the storage bucket holding user verification files, selfies, and private messages was not properly secured – meaning anyone who had the link could access the files without needing a password or authentication.
404 Media verified that the storage bucket link matched one embedded in Tea’s Android app, confirming the source of the leak.
This type of misconfiguration is a common and preventable security issue in cloud-based apps. Without continuous monitoring and strict access controls, sensitive data can be unintentionally left open to the public, creating an easy target for cybercriminals.
Data Security Measures Businesses Need to Have in Place to Prevent This
The Tea app breach is a classic example of a SaaS misconfiguration gone unchecked – a public cloud storage bucket left sensitive user data exposed to the world. Unfortunately, these types of incidents are becoming increasingly common. Misconfigured permissions, public file links, and unsecured cloud storage remain some of the most frequent causes of SaaS data breaches.
To prevent this type of exposure, organizations need to prioritize strong SaaS security measures and proactive data governance. Here are the critical steps every business should have in place:
1. Continuous SaaS Data Monitoring & Misconfiguration Detection
Businesses must actively monitor cloud storage and SaaS applications for risky configurations, exposed links, and sensitive file uploads. In the case of Tea, a publicly accessible Firebase storage bucket – the cloud database where sensitive files were stored – was the source of the breach. With proactive monitoring, this misconfiguration could have been identified and remediated before attackers gained access.
2. Complete Visibility Across SaaS Applications
Organizations need a real-time understanding of where sensitive data lives, who has access to it, and how it’s being shared. Clear dashboards and audit trails enable teams to detect unusual activity and respond before attackers can exploit a vulnerability. Organizations should enforce least-privilege access, ensuring that files and folders are only visible to authorized users. Sensitive customer or user content like personal IDs, verification photos, and private messages should be automatically quarantined or encrypted to reduce risk.
3. Automated Risk-Based Remediation
Even the most careful teams can make mistakes, which is why businesses need automated workflows to quickly address risks and auto-remediate threats as they pop up. This includes removing public links, revoking unnecessary external access, and locking down sensitive files – preventing a small oversight from becoming a widespread data breach.
The takeaway? Data breaches like the Tea app incident are preventable. Continuous monitoring, granular access control, complete SaaS visibility, and automated remediation form the foundation of modern data security. Without these measures in place, misconfigurations and public link mishaps can put both users and brands at serious risk.
Final Thoughts: What the Tea Breach Means for the Future of SaaS Security
This incident is a wake-up call for all social media app users. When apps collect sensitive information, from photos to messages to government IDs, your digital safety depends entirely on the app’s ability to protect its cloud environment.
As apps like Tea continue to rise in popularity, data security must scale with user growth. A breach doesn’t just affect a company’s reputation – it has real consequences and in this case, severe safety concerns.
Data security is synonymous with user trust.
While Tea has since secured its systems, this incident highlights why proactive SaaS data security and access governance are critical.
This breach has taken the world by storm – serving as a reminder that even apps designed to protect people can put them at risk if security isn’t top priority.
Link to original piece: https://www.nbcnews.com/tech/tech-news/women-are-anonymously-spilling-tea-men-cities-viral-app-rcna220681
Want to Learn More?
- See a demo - click here
- Get a FREE Google Workspace Risk Assessment - click here
- See our product in action - click here



.png)