.png)
SaaS tools have transformed how businesses operate – enabling faster collaboration, remote productivity, and seamless data access. But with this shift comes a new class of security challenges: insider threats that operate within your trusted ecosystem.
Unlike external attacks that breach your perimeter, insider threats emerge from users you’ve already granted access to: employees, contractors, or even compromised accounts. In the context of SaaS, these threats are especially hard to detect because they blend in with routine behavior: downloading files, sharing documents, or logging in from different locations.
Traditional security tools often fall short because they focus on network edges or static access rights. But in a SaaS-first world, access is fluid, and identity is the new perimeter.
In this article, we’ll break down how to monitor insider threats in SaaS environments by focusing on behavioral context, identity-aware insights, and adaptive risk scoring. You’ll learn the different types of insider threats, what signals to monitor, and how to respond before sensitive data walks out the door.
What kinds of insider threats do I need to look out for?
Not all insider threats are created equal. In fact, part of what makes them so difficult to detect is that they don’t follow a single pattern. Some insiders act with malicious intent, others simply make mistakes – and some aren’t insiders at all – but external attackers/hackers using an insiders’ credentials.
Here are the three main categories to watch:
1. Malicious Insiders
These are users who deliberately misuse their access to harm the organization. Their goals can include:
- Stealing intellectual property
- Sabotaging systems or data
- Leaking sensitive documents for personal gain or revenge
Example: A disgruntled engineer resigns and downloads proprietary code before their last day, planning to sell it to a competitor.
2. Negligent Insiders
Often overlooked, negligent insiders pose risk through carelessness, not malice. These are well-meaning employees who don’t understand the implications of their actions – like oversharing, setting improper file permissions, or using unapproved apps.
Example: A marketing manager sets a financial forecast file to “Public” in Google Drive, thinking only their team will access it – unknowingly exposing it to anyone with the link.
3. Compromised Insiders
These threats originate from external actors/hackers who hijack legitimate user accounts via:
- Phishing
- Credential stuffing
- OAuth token abuse
Since the activity comes from a legitimate login, these threats are especially hard to detect without behavioral monitoring.
Example: A hacker gains access to a sales rep’s account and begins exporting sensitive customer data, all while appearing as a normal user within your domain.
What should I monitor to detect insider threats in SaaS apps?
Insider threats in SaaS environments often mimic normal behavior: sharing files, granting app permissions, or logging in from a new location. The difference is in the pattern, timing, and context. That’s where contextual monitoring becomes crucial.
Here are the most important signals to watch for:
1. Unusual Login Times or Impossible Travel
If a user logs in during non-working hours, from unexpected countries, or from multiple locations in a short span, it could indicate a compromised account.
Example: An account logs in from New York at 3:15 p.m., and then from Germany at 3:45 p.m. – highly suspicious and impossible.
2. Large File Downloads or Mass Sharing
Look out for sudden and unusual spikes in data movement or actions – especially from users who don’t typically handle large volumes of files.
Example: A quiet HR analyst suddenly downloads 200 documents and shares 50 to a personal Gmail address.
3. Spikes in OAuth or Third-Party App Grants
An increase in OAuth token usage or the sudden appearance of unapproved third-party apps can signal malicious persistence tactics.
Example: A marketing intern connects five new automation tools within an hour, none of which are on the approved app list, and they don’t need these apps to do their job.
4. Access Outside of Role or Department Norms
Users accessing sensitive files or systems beyond their role, scope, or historical behavior should raise flags.
Example: A freelance designer opens the customer support team’s shared drive, even though they’ve never needed that data before and it’s not relevant for their day-to-day work.
5. Former Employees or Dormant Accounts
Inactive or offboarded users with lingering access are a major risk – especially in organizations that rely heavily on tools like Google Workspace, where permissions are rarely revoked at the file level.
Example: A contractor who left six months ago still has access to a shared drive containing customer financials.
It's important to note that none of these actions are inherently malicious on their own, but context allows security teams to discern between what's risky vs. what's not. That’s why effective monitoring needs more than static alerts: it requires identity-aware detection and real-time anomaly spotting that are enriched with context.
The key to detecting insider threats is having a baseline understanding of each user's normal behavior, so that it can be compared to their anomalous and unusual behavior. Not every action is risky, and not every ‘risk’ that shows up in legacy security systems warrants an investigation.
Why are insider threats so hard to detect in SaaS environments?
SaaS environments blur the line between routine and risky. That’s what makes insider threats so difficult to catch without the right context.
Here’s why:
1. SaaS is designed for speed, not scrutiny
Collaboration is the core feature of SaaS tools. Employees can share documents, invite external users, or install new integrations without IT oversight.
Most times, employees aren't thinking of the security implications of using SaaS to collaborate.Their main focus is doing their job and accelerating their own productivity. Inadvertently, this opens the door to accidental or deliberate data exposure.
2. Access is decentralized and often over-permissioned
Many SaaS platforms use flat permission models, where users are granted access by default or inherit it through shared folders and group settings. Over time, this leads to excessive, unchecked access – especially when permissions aren’t manually revoked.
This is particularly risky when contractors or freelancers retain access to sensitive files long after their engagement ends, or when former employees can still reach company data through personal accounts. Without routine access reviews and proper offboarding, these gaps contribute to a sprawling, out-of-control attack surface.
3. Most monitoring tools lack behavioral context
Legacy security solutions were built for static environments: firewalls, VPNs, and perimeter defense – AKA the ways of the past. In SaaS, the “perimeter” is every user. Identity is the new perimeter and every single user seat needs to be carefully watched and monitored.
Context is necessary in order to correlate who that user is and what their actions in SaaS are – this is the only way to get an accurate picture of who is a risky user or not. Security teams need a baseline of contextual user activity so that they can discern a risky action from a normal one. If you can’t tell what’s normal for each identity, how can you detect when something abnormal happens?
4. The threats hide in plain sight
An exfiltration attempt might look like a user sharing files. Credential compromise might appear as a legitimate login. It’s not the action itself that’s suspicious – it’s the when, how, and by whom it’s done!
Without identity and behavior-based context, even advanced alerts can miss real threats, or flood you with noise and false positives.
{{cta-1}}
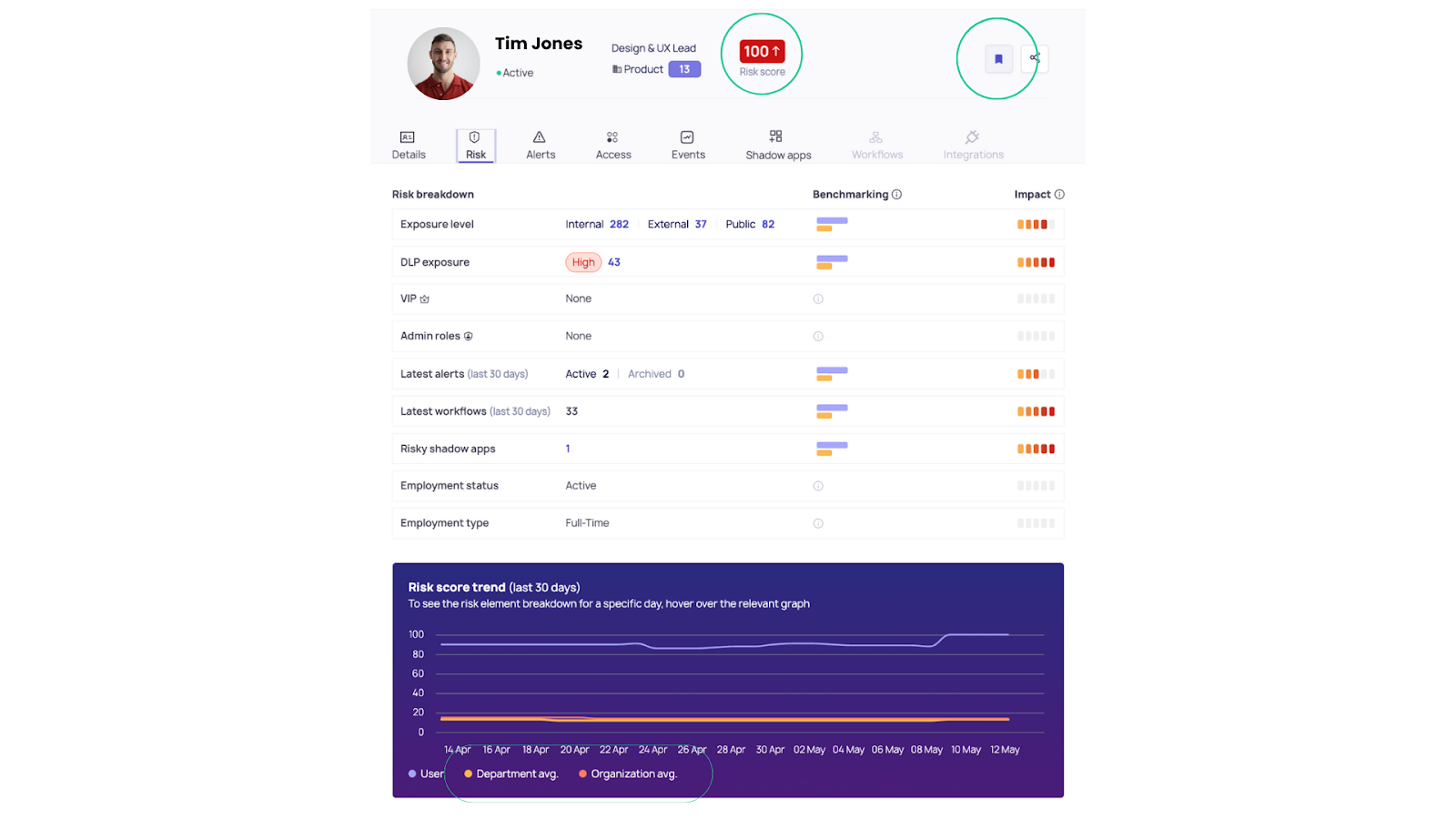
How does DoControl monitor and score identity-based threats?
Traditional security tools focus on events: a login, a file shared, an app connected. But insider threats are rarely about isolated events – they’re about patterns, deviations, and intent. That’s why modern SaaS security demands tools that track identity behavior over time.
DoControl’s Identity Threat Detection and Response (ITDR) framework does exactly that: by building and continuously updating a behavioral risk profile for every user in your SaaS environment.
Here’s how we do it:
Identity Threat Detection & Response (ITDR)
DoControl connects with your existing systems – like HRIS platforms and identity providers – to enrich raw activity data with real-world context. We map user actions across your SaaS stack and tie them back to who the user is, what they typically do, and how their behavior is evolving.
Instead of alerting on every action, we track what’s unusual for that specific user, in that specific role, at that specific time using a contextual risk score.
User Behavior Anomaly Detection
We benchmark each user’s activity against department and role-specific norms. If someone suddenly downloads 500 files, logs in from a new country, or installs unapproved third-party apps, DoControl detects the deviation and surfaces it in real time.
Whether it’s a junior employee connecting suspicious OAuth apps, an admin accessing systems outside their usual scope, or an employee accessing data from an unusual IP, we track and contextualize the risk immediately.

Dynamic Risk Scoring
Each identity is assigned a dynamic risk score that evolves based on behavior, access level, and changes over time. This score isn’t just a number – it’s a prioritization tool for security teams.
It helps you answer key questions fast:
- Should this user be investigated or put on a watch list?
- What users do we need to educate on security best practices?
- Which users are potential insider threats for exfiltrating data?
You can also flag high-risk identities, add them to watchlists, and automate enforcement actions when thresholds are crossed – helping your team move from reactive to proactive.
What should I do when insider risk is detected?
Detection is only half the equation. If you can’t respond quickly and confidently, insider threats will continue to slip through the cracks – or worse, escalate before you act.
The key is having precise, identity-aware response mechanisms that minimize risk without disrupting your business.
Here’s what effective response should look like:
- Targeted remediation: When an identity crosses a risk threshold, you should be able to revoke file permissions, remove OAuth tokens, or suspend access, without affecting unrelated users or teams and slowing down business operations.
- On-demand bulk actions: If an event occurs (like a known compromise), your team should be able to act fast – pulling back access across multiple apps and identities with just a few clicks.
- Automated workflows: Set policies that automatically respond to suspicious activity. For example, instantly revoke sharing for unauthorized users who don't need access to sensitive files.
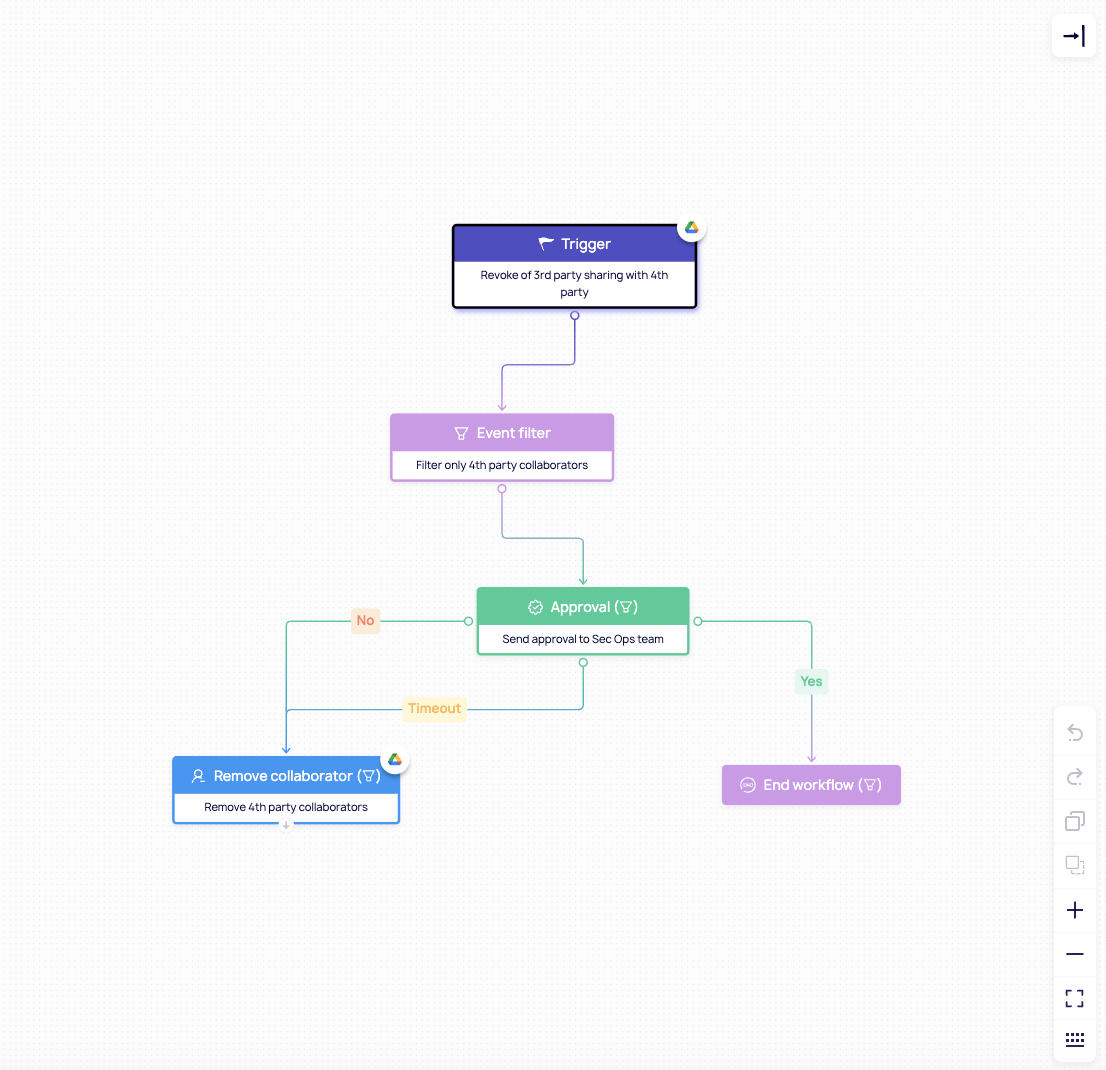
DoControl is built for all of the above, giving you the ability to take action as soon as a threat emerges, while preserving continuity for everyone else.
The goal isn’t just to detect insider threats, it’s to contain and resolve them before they cause damage.
Summary
Insider threats don’t always look like threats – until it’s too late. In SaaS environments where users, data, and access are constantly in motion, relying on traditional tools or surface-level alerts just isn’t enough.
Whether it’s a negligent employee, a compromised contractor, or a malicious insider, DoControl gives you the visibility and control to monitor continuously, act early, and remediate with confidence.
FAQs
1. What is an insider threat in SaaS security?
An insider threat refers to any risk that comes from users within your organization – including employees, contractors, or compromised accounts – who misuse access to SaaS tools to leak, steal, or expose sensitive data.
2. How can I tell if an insider threat is accidental or intentional?
You need behavioral and identity context. Malicious threats often involve unusual access patterns, while accidental ones may involve misconfigurations or careless sharing. Tools that track historical behavior can help distinguish the difference.
3. What tools detect insider threats in SaaS apps?
Modern solutions like DoControl’s ITDR platform monitor identity behavior across SaaS tools, flag anomalies, assign risk scores, and automate responses. These tools go beyond alerts, they provide context and enable security teams to take target actions to contain and remediate the threats when they happen.
4. Can former employees be insider threats?
Yes. If former employees retain access to shared files, folders, or SaaS accounts, they can pose significant risk – especially in environments without strong offboarding workflows or file permission reviews.
5. How can I monitor insider threats without disrupting productivity?
Use identity-aware monitoring that’s built for SaaS. Instead of broad, restrictive controls, these tools provide precise, user-level visibility and action – so only risky behavior is addressed, and everyday collaboration remains uninterrupted.
Want to Learn More?
See a demo - click here
Get a FREE Google Workspace Risk Assessment - click here
See our product in action - click here



.png)