
The modern SaaS data breach rarely begins with malware or sophisticated code. It starts with something far simpler - a login.
The string of data breaches and sophisticated hacks we've seen in the last few months alone proves this.
In June 2025, HR giant Workday was one of them. By impersonating IT and HR personnel, hackers were able to trick employees into handing over personal information and account credentials.
With that data, attackers infiltrated the customer support system, exposing sensitive details from support tickets - names, email addresses, and phone numbers of Workday customers - many of them being very well-known enterprise companies, including more than 60% of the Fortune 500.
Around the same time, there was no shortage of companies falling victim to the string of Salesforce incidents. One of the most notorious was the Salesloft’s Drift breach.
In this breach, a threat actor obtained OAuth tokens that allowed them to impersonate Drift as an authorized third-party app within customer SaaS environments - including Salesforce. With those permissions, they were able to query, extract, and export massive volumes of data from hundreds of Salesforce instances across multiple organizations.
Different companies. Different vectors. But the same pattern: valid credentials abused to gain trusted access.
Identity has become the new perimeter. The question isn’t whether attackers will try to get in - it’s whether your organization can recognize when they already have.
Why Compromised Accounts Are Still the #1 Breach Driver in SaaS
For all the innovation in cybersecurity - from SSO to MFA to zero trust - one problem refuses to go away: stolen credentials remain the easiest way into SaaS environments.
According to IBM’s Cost of a Data Breach Report, compromised accounts continue to account for a large share of breaches worldwide, driving the average cost of a breach to more than $4.8 MILLION per incident. Why is this, and how is it SO common even when organizations know the risk?
1. The rise of AI and social engineering.
Attackers are using AI to personalize phishing at scale - whether it's social engineering like voice cloning, or more sinister like chatbot impersonation and deepfake HR messages. One particularly troubling instance of this was the Workday breach mentioned above.
Employees can no longer tell legitimate requests from fake ones. All it takes is one click to hand over credentials that unlock a SaaS environment.
2. The explosion of SaaS adoption.
The average enterprise now runs hundreds of cloud applications, each with its own permissions, users, and OAuth integrations. Every connection expands the attack surface - and every user identity becomes a potential breach point.
With so many applications and SO much data living in these SaaS apps, it's impossible to monitor every user, every identity, every action, every event, and every data flow without a centralized and automated solution doing so for you.
3. Shadow apps and unmanaged integrations.
Employees often connect unsanctioned apps that connect via OAuth without security oversight. These are what we call shadow apps, and they’ve been a weak link in SaaS security for a long time. Even more frightening (and newly emerging) is the idea of Shadow AI - which are shadow AI apps, browsers, tools, extensions, and even agents that either have over-permissioned scopes or can be classified as ‘non human’ identities.
All of these apps - whether plain shadow apps or shadow AI apps - inherit the same privileges as the human user, which means a single OAuth token theft can expose sensitive data organization-wide, resulting in a million dollar breach.
4. Weak MFA implementation and bypass tactics.
Multi-factor authentication (MFA) has become a household term within most companies, but attackers have adapted faster than most organizations can deploy it. In theory, MFA adds a crucial second barrier to entry. Unfortunately, the way MFA is implemented often creates new opportunities for attackers to slip through.
In SaaS ecosystems, MFA is typically enforced through single sign-on (SSO) or identity providers. But when those same credentials are reused across integrations or lack conditional access controls, one weak link compromises them all.
5. Human nature as the most reliable attack vector.
Technology continues to evolve, but human behavior remains the most persistent vulnerability in SaaS environments. 95% of cybersecurity incidents occur due to human behavior and actions.
Under pressure to stay productive, people naturally prioritize convenience over security. And, most times, employees are simply negligent and security isn't top of mind for them.
Common patterns include password re-use, overpermissioned OAuth approvals, negligence when sharing data…the list goes on. In decentralized SaaS ecosystems, a single mistaken click or over-broad permission can create an identity exposure that ripples across every connected app.
How Attackers Actually Take SaaS Identities
When attackers go after SaaS environments, they’re not breaking in - they’re logging in. Identity compromise has become their preferred access method because it requires no exploits, no malware, and often - no alarms.
The methods vary, but the objective is the same: obtain valid credentials or tokens that grant legitimate access to the SaaS environment and the data that lives there.
1. Phishing and MFA Bypass
Attackers no longer rely on clumsy spam emails that *obviously* look fake. They build convincing, AI-generated messages or fake login pages that look identical to Google Workspace, Microsoft 365, Salesforce, Okta...the list goes on.
Even with MFA in place, prompt bombing or adversary-in-the-middle kits (AiTM) can capture valid session tokens and bypass authentication altogether. Not to mention social engineering and voice-phishing - which is a new emerging tactic that has unfortunately been the culprit this year for several high profile breaches.
2. Credential Reuse and Stuffing
Passwords leaked from unrelated breaches often become the keys to enterprise SaaS platforms. Attackers use automated “stuffing” tools to test those credentials across SSO or identity providers, knowing that one reused password can unlock dozens of connected apps.
3. Malware and Token Theft
Stealer malware quietly harvests saved browser credentials, OAuth tokens, and cookies - selling them on dark web sites where attackers buy access to SaaS accounts at scale. Once purchased, these tokens allow them to impersonate legitimate users for weeks or months.
4. OAuth Abuse and App Impersonation
One of the most insidious tactics in SaaS today involves malicious third-party apps. Attackers trick users into granting OAuth permissions - things like letting these apps “read all files,” “access contacts,” “scan documents” etc…This gives these apps (that can easily be breached!) access and API-level persistence even after passwords are reset.
5. Service Accounts and Non-Human Identities
Long-lived tokens and overprivileged service accounts often lack MFA or monitoring. Once compromised, they offer silent, continuous access to SaaS data pipelines and integrations.
6. AI Agents and Automated Identities
The newest - and scariest - way! As organizations deploy AI assistants and automated agents across SaaS (think Gemini, Copilot, Glean, Claude), each one becomes a potential entry point. Attackers can hijack these agents or their tokens to access sensitive systems - and because they’re “trusted,” most controls don’t flag their activity.
An incident like this JUST happened with Anthropic - and it wasn’t pretty. Attackers leveraged Anthropic’s Claude AI in a new form of “vibe hacking.” They reportedly targeted at least 17 organizations, using AI not just as a tool for automation, but as an active participant in the attack.
Again, attackers don’t need to breach your perimeter - they only need to borrow a trusted identity. And once they have it, the SaaS environment itself becomes the playground.
Key Signals of Risky Identity Behavior to Look Out For
When a third party or non-human identity compromises a SaaS account, the signs rarely (lets be honest - NEVER) start with a flashing alert. They emerge quietly, hidden in plain sight. Attackers often blend into legitimate user behavior, using valid credentials, OAuth tokens, or compromised service accounts to operate under the radar.
That’s why it’s critical to recognize when “normal” activity crosses into abnormal territory. These signals often indicate that an external actor — or an automated identity gone rogue — has gained access to your SaaS environment.
1. Unusual Login Times or Impossible Travel Patterns
If a user’s session suddenly originates from an unexpected geography or device, it’s often a sign of credential theft or token hijacking.
Example: A New York–based engineer logs in during the workday, but within 20 minutes, the same account connects from Europe. That’s not remote work - that’s an intruder piggybacking on a valid session.
2. Access Outside Department or Role Norms
When accounts start interacting with data or applications beyond their defined responsibilities, it’s a red flag that someone else is behind the keyboard
Example: A sales rep suddenly accesses product engineering documents or financial reports - behavior that points to an attacker exploring the environment after gaining valid credentials.
3. Spikes in OAuth Activity or Third-Party App Grants
Compromised accounts often attempt to establish persistence by authorizing new apps or services.
Example: A low-privilege user installs multiple unsanctioned data-sync tools within minutes - a sign of an attacker setting up long-term access through OAuth tokens.
4. Mass File Sharing or Data Downloads
Attackers frequently exfiltrate data through the same sharing features employees use every day.
Example: A typically inactive account downloads hundreds of sensitive documents or shares them with personal email addresses - indicating data theft or preparation for extortion.
5. Dormant or Automated Accounts Reactivated
A service account or offboarded user suddenly active again is a strong indicator of credential compromise or stolen API keys in use.
Example: A decommissioned admin account connects via API, performing privileged actions - often the work of a third party using leaked credentials.
6. Non-Human Identity Anomalies
Machine-to-machine identities can also be hijacked. When a bot or integration starts making unusual API calls, accessing unauthorized datasets, or operating outside defined time windows, it’s likely being manipulated by an attacker.
Example: An AI agent installed for productivity gets breached or goes rouge, taking actions that are extremely out of the ordinary.
How Does A Hacker Steal Data via a Compromised Account?
Once a valid identity is compromised, the rest unfolds fast - often invisibly.
It starts with a legitimate login. The session looks real, the token checks out, and the user’s credentials pass verification. Traditional tools see nothing wrong because - technically - nothing IS wrong!
From there, attackers begin probing the environment: connecting new OAuth apps, sharing data, accessing unfamiliar documents, or reviewing group permissions to see what else the identity can reach. Within minutes, they can escalate privileges or move laterally across SaaS platforms tied together by single sign-on.
Next comes data exploration and exfiltration. Attackers use built-in features - file sharing, report exports, API queries - to quietly siphon and steal data.
Finally, they monetize the access. Some sell the stolen data online. Others extort the organization, leak information publicly, or use the data to compromise downstream partners / vendors (like what happened in Salesforce).
By the time a typical security team spots the anomaly, the damage is done - credentials have been reused, OAuth tokens replicated, and sensitive data already exfiltrated, millions of dollars gone!
The uncomfortable truth: in SaaS, a valid login can be the start of a breach chain that spreads across your entire ecosystem.
How DoControl Detects, Contains, and STOPS These Identity Threats
DoControl’s Identity Threat Detection and Response (ITDR) module is purpose-built to recognize these subtle - but critical - deviations before they evolve into full-scale breaches. Here’s how it bridges visibility, context, and action in real time:
1. Behavioral Baselines Built for SaaS
DoControl continuously benchmarks each identity - human or non-human - against historical activity patterns. When a login, download, or OAuth event breaks from the norm, the system flags and correlates it instantly across your connected SaaS apps.
This means if an external actor logs in using stolen credentials, DoControl identifies it within moments, highlighting what’s abnormal and why it matters.
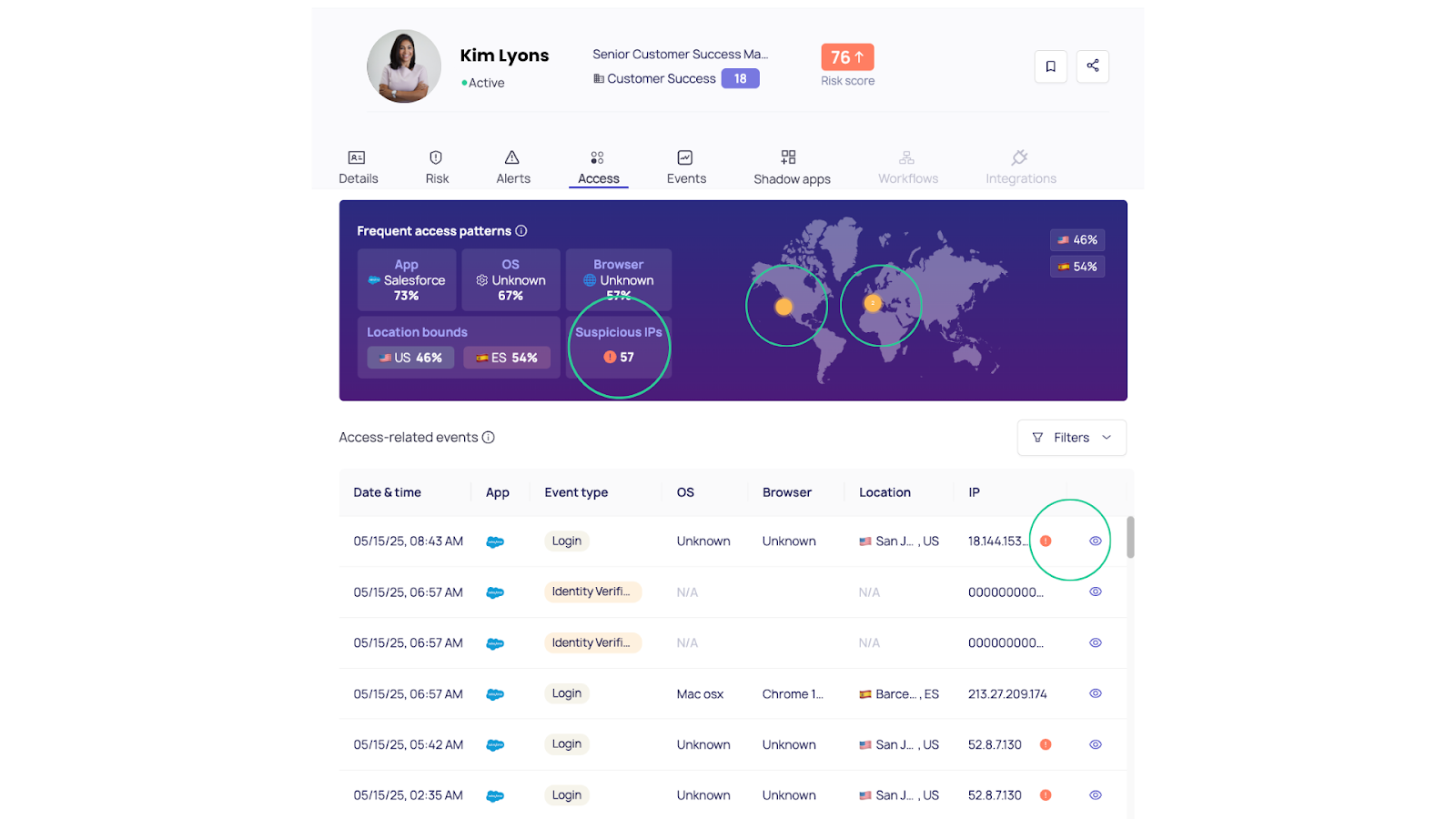
2. Context-Enriched Identity Analytics
Unlike traditional alerting tools, DoControl connects user behavior to business context by integrating with your HRIS and IdP systems.
It knows who a user is, what department they belong to, and what their normal behavior looks like.
When actions fall outside that behavioral baseline - for instance, an HR associate accessing engineering documentation - DoControl surfaces that event as a high-fidelity signal of potential compromise.
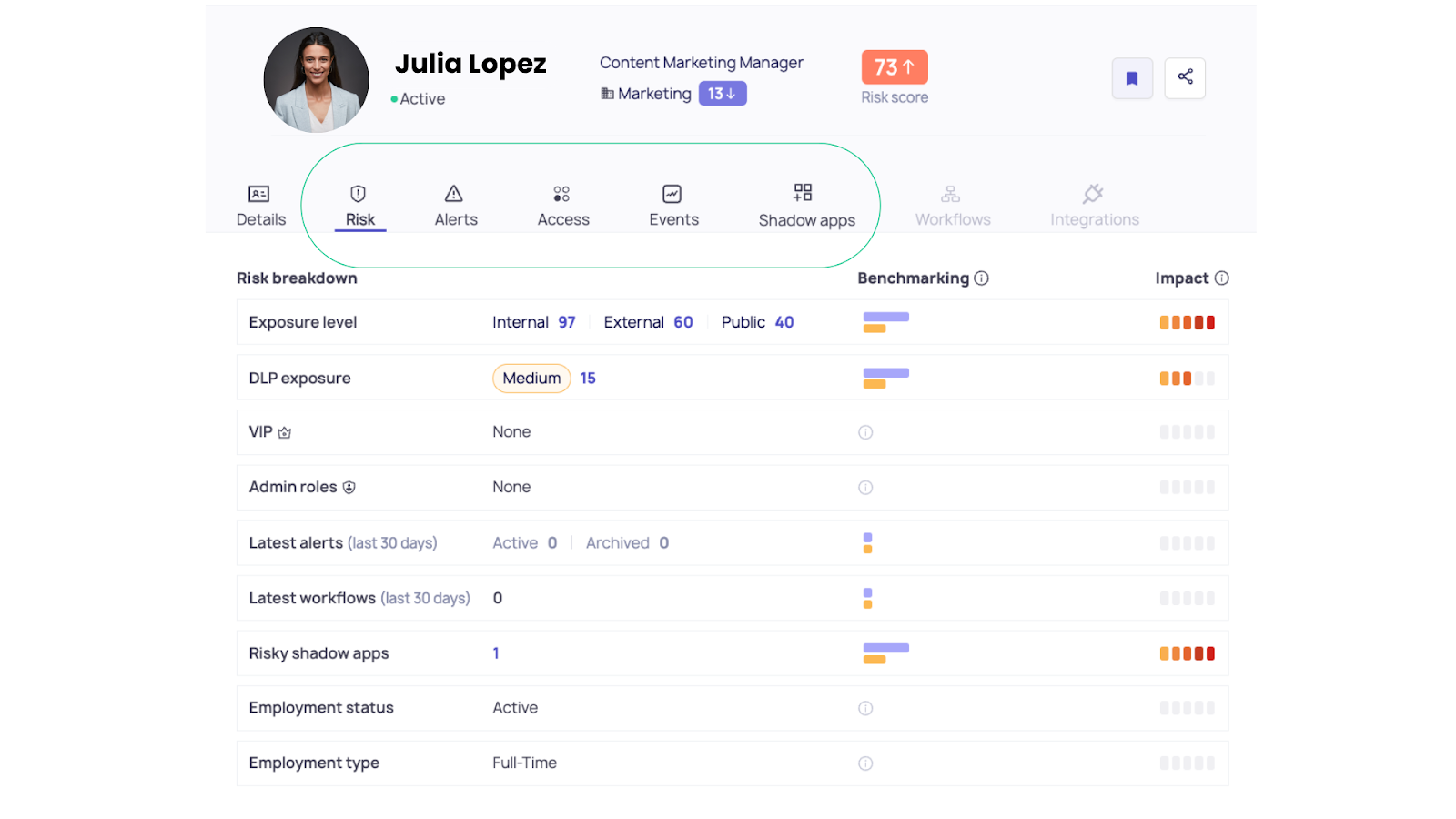
3. Dynamic Risk Scoring That Evolves With Behavior
Each identity’s risk score updates in real time as new actions occur. If an attacker begins probing data or linking unauthorized apps, their risk profile spikes instantly, prompting automated workflows or analyst review.
This ensures security teams focus only on meaningful risk, not a flood of generic alerts, all while pinpointing WHO the risky user is.
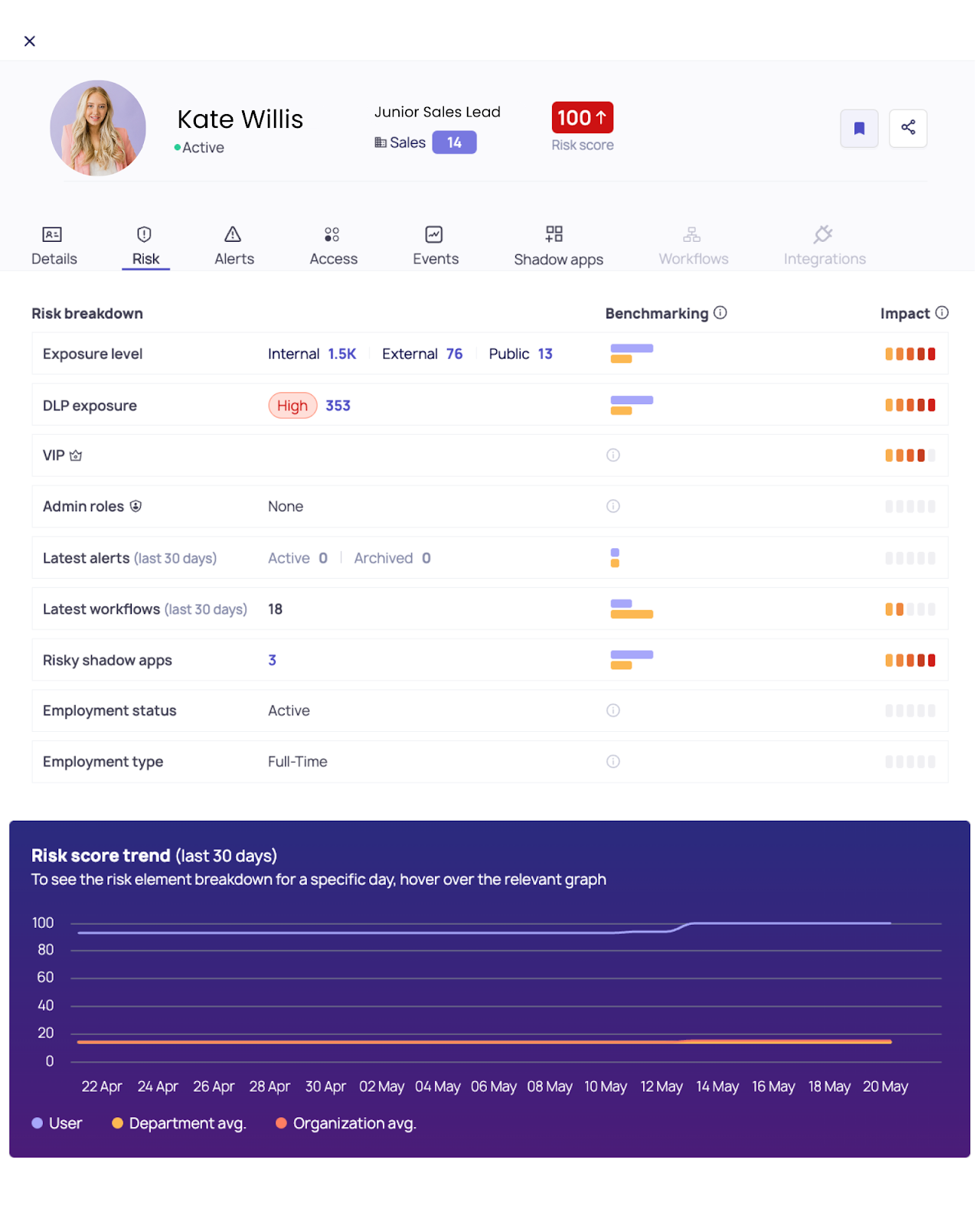
4. Real-Time Containment and Remediation
Visibility and detection without response isn’t enough, and many SaaS security vendors stop here. But not DoControl. DoControl enables both automated and on-demand controls the moment suspicious activity is detected:
- Auto-revoke OAuth tokens or session keys used by compromised accounts
- Temporarily suspend user access to affected apps or data
- Instantly block large downloads or public shares in progress
- Initiate bulk remediation to reset passwords or re-authenticate users
For identity takeovers involving third-party access, DoControl can cut the connection mid-session, stopping exfiltration AS it happens - not after the fact.
5. Precision Response Without Business Disruption
Remediation happens at the user level, allowing security teams to contain a compromised identity via an automated workflow running in the backend. This means that the compromise gets cut off without stopping entire workflows, disrupting teams, or derailing business ops.
For example, if a contractor’s account behaves suspiciously, DoControl can isolate their access automatically while leaving the rest of the organization unaffected.
Conclusion
By combining contextual identity insight, real-time behavioral monitoring, and automated response, DoControl ensures that even the stealthiest third-party account takeover doesn’t go unnoticed - or unanswered.
Every identity action is observed, evaluated, and controlled through one platform, giving security teams full command of who’s accessing what, from where, and why - before attackers ever get a foothold.
The most dangerous thing about a compromised account isn’t the breach itself - it’s how ordinary it looks while it’s happening: a legitimate login, a trusted OAuth token, a familiar user performing familiar actions…By the time traditional tools realize something’s wrong, data has already moved, attackers have already blended in, and the damage is done.
This is the reality of modern SaaS: identity is both the access point and the attack surface.
The only effective defense is one that sees every identity in context. That’s where DoControl redefines SaaS security.
By combining continuous visibility, behavioral analytics, and automated remediation, DoControl’s Identity Threat Detection and Response (ITDR) ensures you can detect the subtle signals of compromise and stop the breach before it spreads.
With us as your SaaS data solution, security teams finally gain what attackers hope you’ll never have: true control.



