
In today’s SaaS-driven workplace, collaboration is faster than ever - but so is the risk of data exposure. Tools like Google Workspace, Slack, and Microsoft 365 make it easy for employees to share files, links, and conversations across teams, partners, and customers.
Unfortunately, that same ease of use often leads to oversharing of sensitive documents - whether through misconfigured permissions, “anyone with the link” settings, or careless sharing in chat channels.
For security professionals, this oversharing is more than a nuisance; it’s a critical risk factor. 95% of cybersecurity incidents occur due to human error, with 76% of organizations detecting increased insider threat activity over the past five years.
The challenge for CISOs, IT leaders, and SaaS security practitioners is clear: how do you enable collaboration while ensuring sensitive information stays protected?
The Risks of Oversharing Sensitive Documents in SaaS
Oversharing sensitive documents can open the door to data leaks, regulatory violations, and reputational damage. In a SaaS environment where employees can instantly share files across the globe, even a single misstep can have massive consequences.
Common Oversharing Scenarios
- Google Drive “Anyone with the link” sharing - An employee shares a spreadsheet externally without realizing it’s open to the public.
- Slack messages with external collaborators - Sensitive financial data or customer records are posted and sent around in Slack channels that include third parties.
- Forgotten public files - Documents that were once shared for a project remain publicly accessible and even get indexed by search engines.
Business and Security Impact
When sensitive files are overshared, attackers don’t need to hack in - they simply stumble upon exposed data. This is how many of the most dangerous breaches begin. The consequences can include:
- Data exposure and leaks (customer information, intellectual property, financial data).
- Regulatory noncompliance with frameworks like GDPR, HIPAA, and SOC 2.
- Reputational harm when customers or partners lose trust in your ability to protect their data.
One of the most notorious examples of this was the recent $14B ScaleAI breach. ScaleAI, a high-profile startup (recently valued at $14.8 billion in a deal with Meta), used public Google Docs with "Anyone with a link can access” sharing permissions to store and share extremely sensitive information related to clients like Meta, Google, and Elon Musk’s xAI.
Thousands of documents were found public, including AI training materials, internal ratings of employees, pay information and contractor emails, confidential manuals from Google and Meta, and more.
Despite these documents being labeled “confidential,” they were exposed to anyone who stumbled across a link - or was sent one.
As shocking as this sounds, this happens all the time.
For organizations relying heavily on SaaS applications, oversharing isn’t just an accident waiting to happen - it’s a top SaaS security risk that demands proactive prevention.
Why Employees Overshare Sensitive Information
Employees remain the primary source of oversharing incidents. The issue usually isn’t malice - it’s a mix of human behavior, workplace pressures, and limited visibility. To understand the risk, it helps to break it down into three types of insider activity.
1. Lack of Security Awareness
Oversharing often stems from employees simply not realizing the security implications of their actions. These are called negligent insiders. Negligent insiders are just as harmful as malicious insiders (employees who mean to cause harm), or compromised insiders (employees who have been hacked and are being impersonated).
Negligent insiders are by far the most common sources for oversharing in 2025. These are well-intentioned employees who accidentally expose sensitive data. This is mostly because there is a lack of awareness of the risks to oversharing.
For example, instead of sharing a file directly with a coworker, they set permissions to “Public - anyone with the link”, inadvertently leaving salaries, budgets, or customer data exposed. Though unintentional, negligence can cause just as much damage as malicious activity.
While malicious and compromised insiders pose obvious threats, it’s the negligent insider that represents the biggest blind spot for most organizations. These are your everyday employees, doing their jobs - but in ways that unintentionally put sensitive data at risk.
2. Convenience Over Security in Collaborative Environments
Modern teams thrive on speed - especially companies operating in Google Workspace or Slack that were born within the last 15 years. It's embedded in their culture to move quickly and get things done.
When deadlines loom, convenience often outweighs caution. One of the most common examples is users setting documents to “Anyone with the link” in Google Drive or Slack file shares.
The logic is simple: instead of sending a file, waiting for access requests from managers or other peers, and then waiting for them to manually approve them, employees flip permissions to “Anyone with the link” so work doesn’t get delayed.
The intention is good - to keep projects moving quickly! - but the result is uncontrolled access that can extend far beyond the intended audience.
This small trade-off between speed and security often goes unnoticed, yet it’s one of the leading causes of sensitive document oversharing in SaaS environments.
3. Poor Visibility and Controls: The Need for Granularity
Another driver of oversharing is the lack of granular access controls in many organizations. Traditional sharing permission models & data loss prevention tools operate at a binary level - either grant access or block it - with little nuance or customization. But, modern SaaS ecosystems demand more context and precision.
Granular controls let security teams define:
- Who can access resources (ex. third-party contractors vs. full-time employees).
- What files, folders, or data types they can see (ex. Should this employee have access to this PII? Is this access appropriate with their role at the company?)
- Which app integrations they can authorize (ex. Should this user be able to connect to this app? What OAuth scopes are appropriate?)
- When and where access is valid (ex. Should this access be revoked after 7 days? Is this IP address signaling unusual login activity?.
- Why access is being granted, based on context and behavior (ex. Does this access or share make sense in the context of this employee's role or function at the company? Or, is it completely random?)
This matters because SaaS environments are messy: thousands of users, apps, and files in motion at all times. Without fine-grained governance, oversharing incidents slip through the cracks. Granular controls make it possible to enforce policy without stifling productivity - ensuring sensitive data stays protected at SaaS scale.
Put simply: oversharing happens because employees are human, collaboration is fast, and controls are often blunt. To prevent it, organizations must address all three drivers: awareness, pressure, and visibility.
Compliance & Regulatory Considerations in Oversharing
When employees overshare sensitive documents in SaaS platforms, the consequences extend far beyond data breaches and reputational damage (although these are HUGE!). They also can directly threaten an organization’s ability to remain compliant with critical regulations.
Each framework sets specific requirements around data access, sharing, and protection - and violations often carry heavy financial, legal, and reputational consequences.
→ SOC 2: Oversharing sabotages the strict controls auditors look for when validating a company’s ability to safeguard data. If sensitive customer contracts or financial files are broadly accessible or publicly shared, auditors will flag gaps that could jeopardize SOC 2 certification.
→ ISO 27001: This global standard emphasizes well-defined access controls and secure information management. Broad or unmonitored file sharing directly violates those principles. The result can be failed audits, loss of certification, and diminished credibility in highly competitive markets.
→ HIPAA (Health Insurance Portability and Accountability Act): A single overshared Slack file containing PHI (like medical records or billing data) is considered a violation. Healthcare organizations have seen fines ranging from tens of thousands to millions of dollars for this type of incident - not to mention the reputational fallout in an industry where patient trust is everything.
These are just three examples, and there's many more compliance standards to look out for.
The real-world impact of oversharing is not just about exposed data - it’s about lost revenue, broken trust, regulatory fines, and damaged reputations.
To prevent this, organizations need SaaS security providers that can monitor file-sharing activity, benchmark against compliance frameworks, and enforce controls in real time.
Best Practices to Prevent Document Oversharing
Security teams should adopt a set of practical, repeatable best practices that balance productivity with protection.
1. Educate Employees on Secure Sharing Practices
Training employees is the first line of defense - especially when the majority of workplaces are dealing with negligent insiders.
Employees should understand what constitutes sensitive data, how sharing permissions work in platforms like Google Workspace and Slack, and oversharing creates risk. Regular refreshers help turn secure sharing into second nature.
2. Enforce Access Controls
Despite education being an important step, its obviously not enough in 2025. Humans are exactly that: humans. And error is bound to happen. This is why organizations need to apply the principle of least privilege to document access.
Limit file permissions to only those who need them, enforce expiration dates on shared links, and require authentication for external collaborators. Access should never default to “Anyone with the link.”
3. Automate Data Access Governance
Manual intervention, investigation, and clean up is simply not feasible for most midmarket to enterprise companies who are trying to scale their business and operations. Manual work from security teams can’t keep pace with SaaS environments and how quickly data moves.
Organizations need automation to continuously monitor file-sharing activity, flag risky behavior, and remediate permissions in real time. Automated data access governance ensures policies are applied consistently, without slowing collaboration.
4. Deploy SaaS Security Policies
This all sounds great - but how do I even instill granular access controls or automate data access governance at scale? Well, the next step is to partner with a vendor who specializes in SaaS security: one who can implement contextual data loss prevention (DLP) to prevent sensitive documents from being shared inappropriately.
These DLP policies should be context-aware. Every sharing action should be evaluated based on the user, the file, and the purpose behind the activity. By enriching each decision with this context, security teams can reduce false positives and focus on the actions that actually pose risk.
The result of this is stronger protection where it matters most, without unnecessarily blocking safe collaboration or slowing down business operations.
How DoControl Prevents Oversharing of SaaS Data
Preventing oversharing requires controls that go beyond detection - organizations need automated governance that adapts to how people actually work. DoControl addresses these challenges with capabilities that eliminate oversharing by design.
1. Time-Bound Sharing: Granular Policies That Expire Risk by Default
One of the most persistent risks in SaaS environments is uncontrolled, long-term external access. In Google Drive, for example, a file shared with a vendor may remain accessible months or even years after the engagement has ended.
With DoControl, organizations can implement time-based access policies that prevent this problem at the source:
- Auto-expire links after 7, 30, 60, or 90 days.
- Re-engage file owners via Slack or email to confirm whether sharing is still needed - automatically revoking access if it’s not.
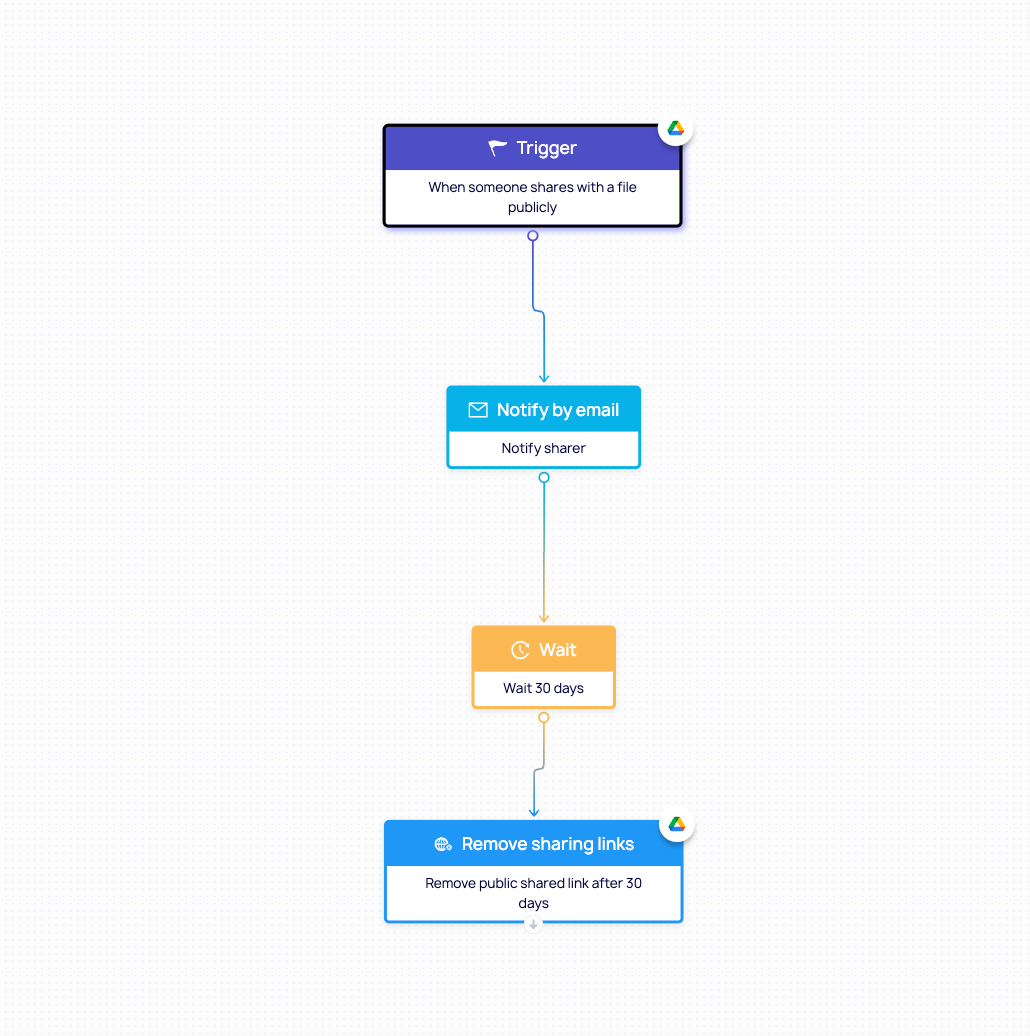
Instead of depending on manual reviews or hoping someone remembers to clean up permissions, DoControl bakes risk expiration into the workflow, reducing exposure while keeping collaboration smooth.
2. Policy-Driven Remediation and Enforcement
DoControl goes a step further by offering policy-driven remediation at scale. With no-code workflows, organizations can automatically enforce governance strategies without slowing down the business. Examples include:
- Removing public or external access to sensitive files in real time.
- Restricting file sharing based on sensitivity, department, or user risk level.
- Requiring manager approval for external shares or large-scale downloads.
- Revoking file ownership automatically during employee offboarding.
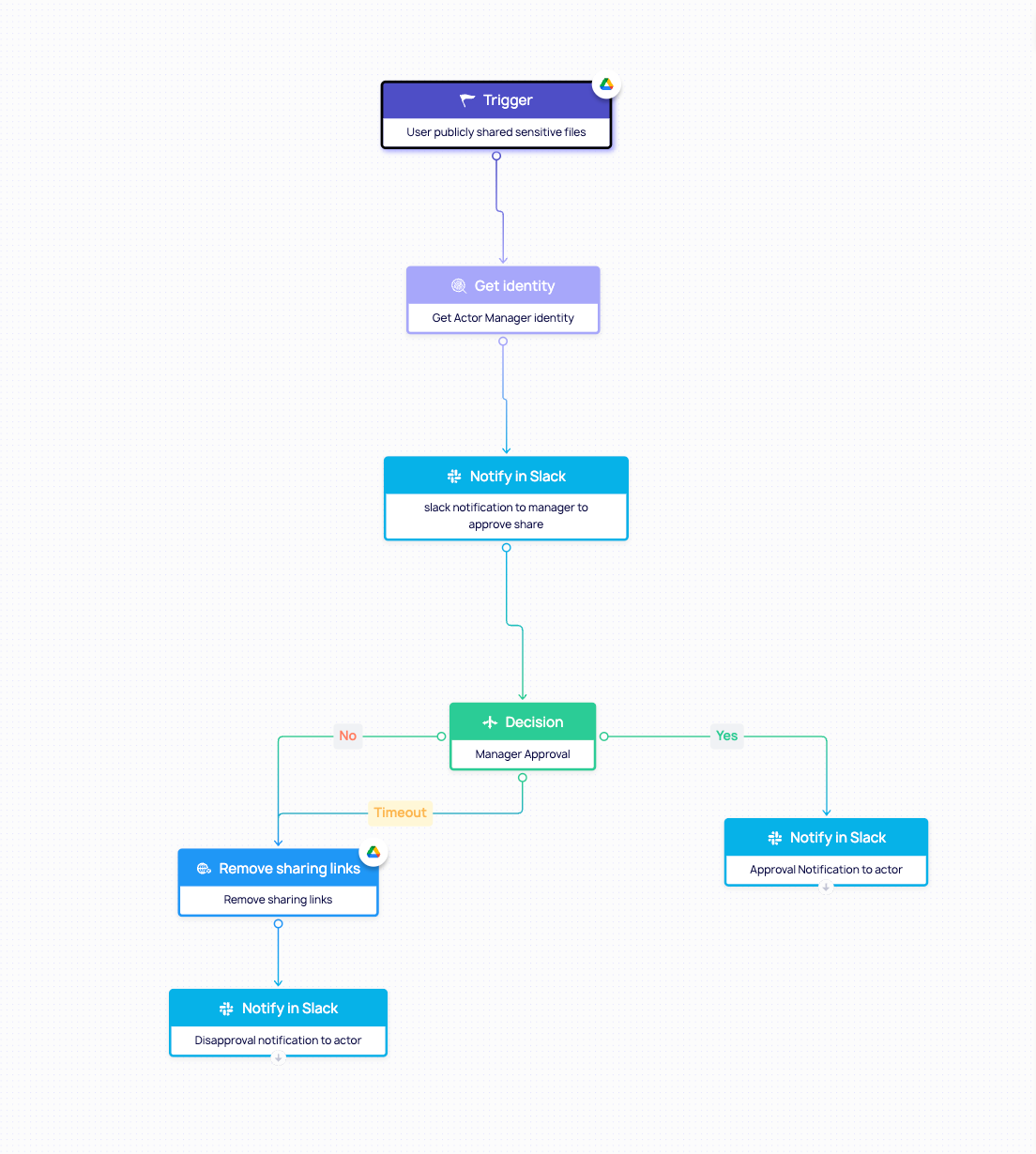
These controls reduce the burden on end users, accelerate incident response, and strengthen the organization’s security posture - all without creating unnecessary friction for day-to-day work.
3. Data Scanning and Classification: Identifying Sensitive Data at Scale
Detecting oversharing isn’t just about knowing who shared a file - it’s about understanding what’s inside. DoControl brings deep visibility into SaaS environments with 230+ pre-built data classifiers that automatically scan files for sensitive content.
This includes detection for:
- Personally Identifiable Information (PII) such as SSNs, driver’s license numbers, and passport details.
- Financial data like credit card numbers, payroll files, and budget spreadsheets.
- Regulated information tied to compliance frameworks like HIPAA and GDPR.
…and more. Basically, any type of sensitive data type you have - we can detect.
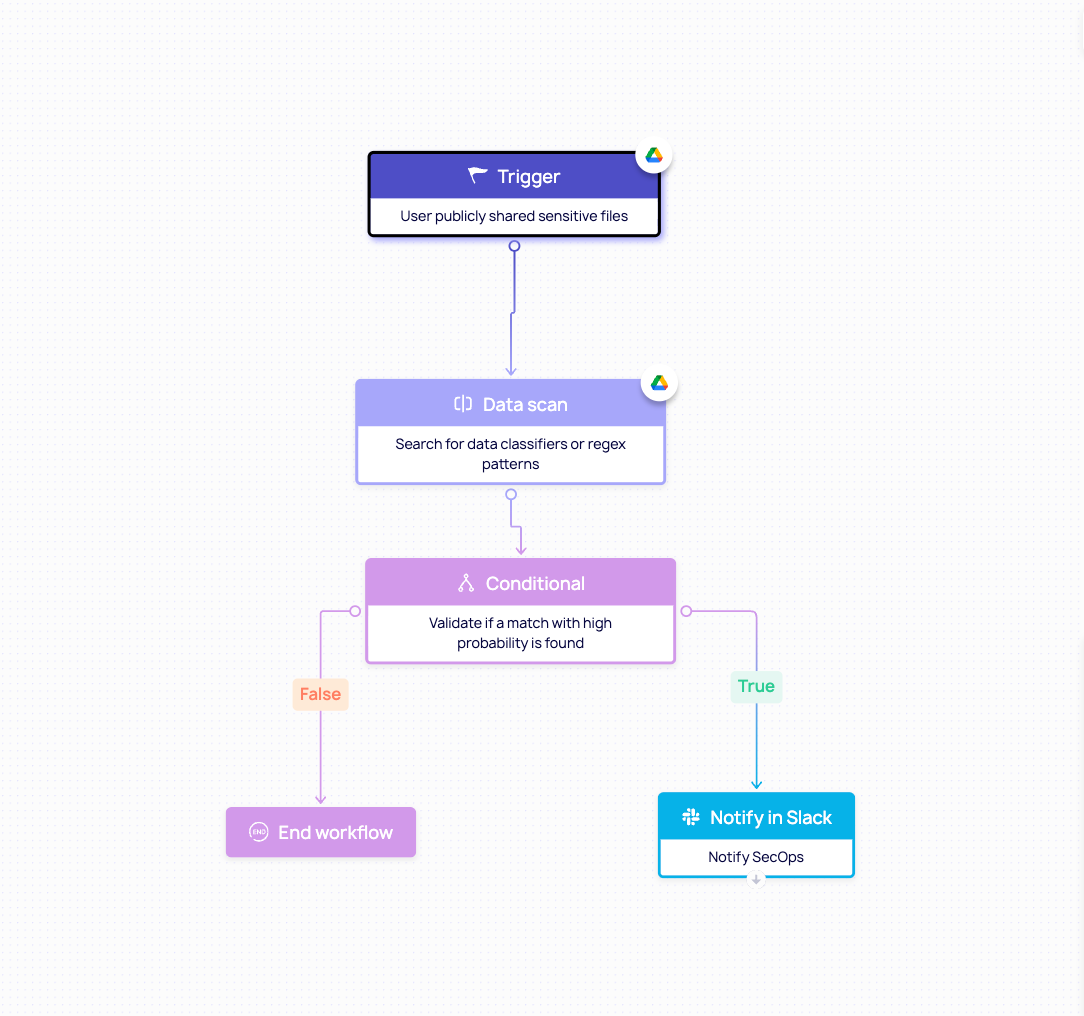
This only scratches the surface in how DoControl protects and prevents oversharing in SaaS environments. Our DLP, insider risk management, and data access governance capabilities give organizations the complete visibility, customization, and control to effectively manage and protect their SaaS data.
Summary
Oversharing sensitive documents is one of the most common - and most dangerous - risks in modern SaaS environments.
The good news: preventing oversharing doesn’t mean slowing down business. By educating employees, enforcing access controls, automating governance, and deploying SaaS security policies, organizations can strike the right balance between collaboration and control.
Platforms like DoControl bring this all together, granting your security teams the visibility and automation needed to keep SaaS environments secure, compliant, and resilient - without disrupting productivity.
Want to Learn More?
- See a demo – click here
- Get a FREE Google Workspace Risk Assessment – click here
- See our product in action – click here



