
As organizations continue to rely on SaaS applications for core business operations, SaaS security is entering a new phase. In 2026, security teams are facing growing challenges around identity abuse, data sprawl, AI-driven workflows, and increasing complexity across SaaS environments.
This article outlines the top SaaS security trends to watch in 2026, based on industry observations, conversations with security leaders, insights from analysts, and evolving attack patterns. Each trend highlights where organizations are seeing increased risk and what security teams should pay attention to as they plan for the year ahead.
1) Former employees are becoming the leading source of SaaS data exfiltration
Former employees are emerging as one of the most common sources of SaaS data exfiltration. Unlike traditional insider threats, this risk is often unintentional or opportunistic, enabled by lingering access, shared links, and data copied before or during offboarding.
Employee turnover is increasingly responsible for data leaving organizations - often through legitimate access that was never fully revoked. Or, *most* of this exfiltration happens BEFORE onboarding. Employees share files and data to their personal accounts while still at their company in preparation for leaving.
How this risk shows up in SaaS environments
- Sensitive files are shared, downloaded, or exported before an employee’s departure
- Access to SaaS applications remains active after offboarding
- Shared links and external collaborators are not removed when an employee leaves
- Data is forwarded via Drive or Slack to personal emails or AI tools
- Former employees continue accessing data through unmanaged devices
What security teams should look out for
- Lack of centralized visibility into where sensitive data lives
- Current employees sharing data to personal accounts or external domains
- Unusual data downloads or sharing activity near exit dates
- Data access that happens out of context or doesn't make sense based on that users role, scope, or responsibilities
- SaaS access that persists after termination or role changes
2) Employees remain the most targeted and most effective SaaS attack vector
95% of security incidents happen as a result of human behavior and user actions. Despite advances in security tooling, employees continue to be the primary entry point for SaaS data exfiltration breaches due to their access, permissions, and daily interaction with sensitive data.
How this risk shows up in SaaS environments
- Negligent employees sharing documents publicly or with ‘Anyone with the link’ can access permissions
- Oversharing of files, folders, and dashboards with external users or contractors - and never unsharing once the work is done
- Phishing attacks that lead to compromised SaaS accounts and result in stolen data
- Credential reuse across personal and corporate accounts
- Accidental exposure of sensitive data through collaboration tools or shadow AI
What security teams should look out for
- Employees accessing data that doesn't make sense for them based on their role, scope, department, responsibilities, etc.
- Users sharing data too broadly, sharing with personal accounts, or external domains
- Repeated phishing or credential-based alerts tied to SaaS access
- Frequent external sharing of internal data that should not be public facing
- Inconsistent enforcement of least privilege across SaaS apps and connecting to third-party tools via OAuth
3) Organizations are realizing data classification alone is not enough without actionability
While many organizations have invested in data classification, they are finding that visibility without enforcement (simply knowing what their data is labeled as with no way to actually remediate that data) is useless and does nothing to reduce SaaS data risk.
How this risk shows up in SaaS environments
- Sensitive data is classified, but still widely accessible and proper controls are in place
- Security teams lack the ability to block, revoke, or restrict risky actions
- Alerts are generated without clear remediation paths or next steps
- Data remains exposed through sharing links and integrations
- Classification tools operate in isolation from access controls or remediation workflows
What security teams should look out for
- Classified data with unrestricted access or sharing
- Alerts that are acknowledged but not acted upon
- Manual remediation processes that do not scale
- Disconnected tooling between data discovery and control
- Inability to prioritize risk based on data sensitivity
4) Non-human identities must be governed as rigorously as human users
Non-human identities such as AI agents, service accounts, API tokens, and automation tools now have persistent access to SaaS environments, often without the same oversight as human users.
How this risk shows up in SaaS environments
- Service accounts with broad, long-lived permissions
- API tokens that are never rotated or reviewed
- Automation tools accessing sensitive data without monitoring
- Lack of ownership or accountability for non-human identities (AI agents)
- Non-human access that bypasses traditional security controls
What security teams should look out for
- Non-human identities with excessive permissions
- Credentials that do not expire or rotate
- Limited visibility into what non-human identities can access
- Missing audit trails for automated actions (especially when agents are involved)
- Orphaned service accounts tied to deprecated workflows
5) OAuth abuse is emerging as a primary SaaS attack vector
OAuth-based access is increasingly being exploited to gain persistent, legitimate-looking access to SaaS applications without compromising user credentials.
How this risk shows up in SaaS environments
- Users granting excessive OAuth permissions to third-party apps
- Malicious or compromised integrations accessing sensitive data
- OAuth tokens enabling lateral movement across SaaS tools
- Limited visibility into active OAuth grants and scopes
- Difficulty revoking access once tokens are issued
What security teams should look out for
- Newly authorized third-party applications
- OAuth apps (especially AI apps) requesting high-risk scopes
- Tokens with long lifetimes and broad access
- Inactive or unused integrations that remain enabled
- Lack of regular review of OAuth permissions
6) SaaS data sprawl is increasing and becoming as critical as app sprawl
As organizations adopt more SaaS applications, sensitive data is spreading across platforms, users, and integrations, making it harder to track and protect. This is commonly referred to as SaaS data sprawl.
- Sensitive data being shared across multiple SaaS tools (for example, Google Drive links shared in Slack or Microsoft 365 files shared through Box)
- AI tools like Gemini being able to surface and locate sensitive data in Google Workspace when access controls are not regularly reviewed or updated
- Inconsistent security controls applied across different SaaS platforms
- Lack of clear ownership over where critical data is stored
- Data moving freely between SaaS applications through integrations
What security teams should look out for
- Sensitive data appearing in multiple SaaS tools without clear business justification
- AI tools accessing or exposing sensitive data due to overly broad or outdated permissions
- Gaps in security controls between SaaS platforms handling similar types of data
- No defined data owners for sensitive or regulated datasets
- Integrations that allow sensitive data to move between apps without oversight
7) Browsers are not sufficient to secure modern SaaS environments
The enterprise browser has become the primary way users access SaaS applications, but it was never designed to enforce consistent, data-aware DLP across SaaS environments. As a result, organizations relying on browser-based controls alone struggle to prevent sensitive data exposure and misuse.
How this risk shows up in SaaS environments
- Limited visibility into how sensitive data is accessed, copied, or shared inside SaaS apps
- Sensitive data being copied, downloaded, or shared directly through the browser
- Rigid controls that do not match the complexity and collaborative nature of SaaS environments
- Gaps in visibility into user actions and behavior after authentication
- Session hijacking and token theft occurring within browser-based SaaS sessions
- Browser extensions accessing or extracting sensitive SaaS data
What security teams should look out for
- Lack of visibility into sensitive data access, movement, and sharing across SaaS applications
- Sensitive data leaving SaaS environments through browser-based actions without DLP enforcement
- Browser-based controls that are too inflexible to support SaaS collaboration without increasing risk
- Limited insight into user behavior once authentication is complete
- SaaS sessions that appear valid but may be compromised through token or session theft
- Browser extensions with unnecessary or high-risk access to SaaS data
8) Data loss prevention is becoming a full program, not a single solution
As SaaS environments grow more complex, organizations are recognizing that data loss prevention cannot be addressed with a single tool or control - but rather, it needs a full program that has multiple different solutions that close different gaps.
How this risk shows up in SaaS environments
- DLP tools operating in silos without shared context
- Sensitive data exposed despite being “covered” by a DLP product
- Expecting one DLP tool to handle SaaS DLP, email DLP, endpoint DLP, and more
- Inconsistent enforcement across different SaaS applications
- Gaps in protection because a single DLP tool cannot cover every use case
What security teams should look out for
- DLP controls that are fragmented across identity, data, and SaaS applications
- Sensitive data incidents occurring even when DLP policies are in place
- Overreliance on a single DLP tool for multiple environments and workflows
- DLP policies that are enforced unevenly across SaaS platforms
- Persistent coverage gaps that indicate the need for a broader DLP program
9) AI adoption is increasing SaaS configuration drift
The rapid introduction of AI features, integrations, and automation is accelerating configuration changes across SaaS environments, often without proper oversight.
How this risk shows up in SaaS environments
- New AI features enabled by default with permissive settings
- Integrations added quickly to support AI workflows
- Configuration changes made outside formal change management
- Security settings reverting or drifting over time with no way to automatically detect and correct
- Increased complexity across permissions, sharing, and access
What security teams should look out for
- Frequent or undocumented configuration changes
- AI-related features accessing sensitive data by default
- Drift between approved and actual SaaS configurations
- Limited visibility into configuration changes over time
- Reliance on periodic checks instead of continuous monitoring
10) SaaS supply chain attacks are increasing in frequency and impact
2025 was the year of supply chain attacks. Organizations have been increasingly relying on third-party SaaS vendors, integrations, and plugins, expanding the attack surface beyond their direct control. Now, companies are opening their eyes.
How this risk shows up in SaaS environments
- Vendors or partners become compromised, allowing attackers to access customer environments
- Third-party integrations are granted broad permissions to sensitive data
- Sensitive data is shared or processed through external platforms
- Limited visibility into vendor security posture or vendor breaches
- Delayed detection of downstream exposure increases overall impact
What security teams should look out for
- Third-party vendors or partners with access to internal SaaS environments
- Integrations with excessive or unnecessary permissions
- Sensitive data being shared with external platforms or partners
- Lack of ongoing visibility into vendor security posture and incidents
- Difficulty identifying scope and impact when a vendor is breached
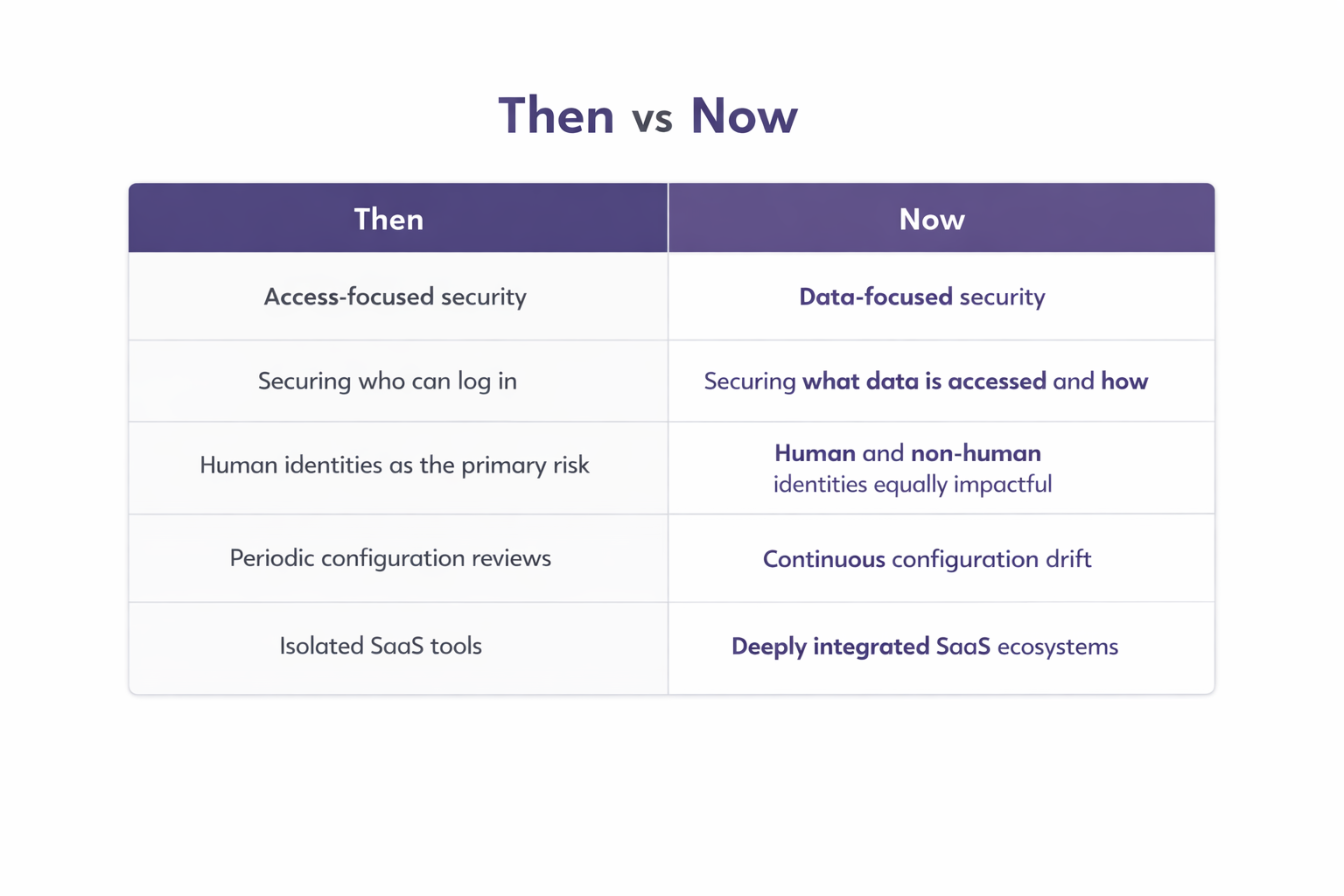
How SaaS security in 2026 differs from previous years
SaaS security in 2026 looks fundamentally different from just a few years ago. While earlier approaches focused on access and perimeter-style controls, today’s risks are driven by data movement, identity sprawl, and constant change across SaaS environments.
How DoControl helps security teams reduce SaaS data risk in real time
Modern SaaS security requires more than visibility - we believe that visibility without control is useless. True SaaS security requires understanding context and taking action at the moment risk appears.
DoControl is built to help security teams:
- Enforce ITDR policies (detect, monitor, and control all identities)
- Enable robust data access governance and SaaS DLP (continuously govern and protect data)
- Control shadow apps + shadow AI (remediate Oauth exposure)
- Ensure full compliance (automatically detect and fix configuration drifts)
Identity risk detection and insider threat response (ITDR)
DoControl analyzes identity behavior in the context of data access, not just by events. By understanding who an identity is, their role in the organization, what data they typically access, and how they normally behave, security teams can distinguish legitimate activity from risky or anomalous behavior.
This context-aware approach allows teams to detect insider risk, compromised accounts, and misuse by both human and non-human identities. When behavior falls outside an expected scope, DoControl enables real-time remediation - such as restricting access, revoking sharing, or triggering automated workflows - before data exposure escalates.
Data access governance
DoControl continuously monitors sensitive data across SaaS applications to understand where it lives, who has access to it, and how it is being shared. Instead of relying on point-in-time reviews, security teams gain ongoing visibility into data movement and exposure.
When risky access or sharing is detected, teams can take immediate action through automated remediation, ensuring that misconfigurations, oversharing, or unauthorized access are corrected quickly and consistently across environments.
Data loss prevention with automated workflows
DoControl approaches DLP as an active enforcement layer rather than a passive alerting system. By combining data context with identity behavior, teams can define automated workflows that respond to real-world risk scenarios.
This includes automatically restricting sharing, revoking access, or notifying sec teams or managers when sensitive data is exposed or misused. These workflows allow security teams to reduce response time, minimize manual intervention, and ensure consistent enforcement across SaaS platforms.
Shadow apps and shadow AI governance
DoControl provides visibility into unsanctioned SaaS applications, third-party integrations, and AI tools that interact with organizational data. Rather than simply flagging shadow usage, DoControl offers recommended remediation steps based on risk and data sensitivity.
Security teams can remove or restrict access, apply policies, and establish automated workflows to prevent similar risks in the future - balancing governance with business productivity.
Misconfiguration detection and automated remediation
As SaaS configurations change over time, DoControl helps teams identify configuration drift and security gaps that increase data exposure. Continuous monitoring enables detection of risky sharing settings, excessive permissions, and misaligned configurations.
Through automated remediation workflows, security teams can correct misconfigurations at scale, reducing reliance on manual checks and ensuring that security posture keeps pace with ongoing SaaS changes.
What security teams should do next
In 2026, effective SaaS security requires a shift from securing access alone to securing data and behavior across environments.
Identity controls remain important, but they are no longer sufficient on their own. Security teams must focus on understanding where sensitive data lives, how it moves, and who or what can access it.
Before adding new tools, organizations should prioritize visibility into SaaS data, identities, integrations, and configurations.
With clear visibility, teams can make better decisions about enforcement, remediation, and risk reduction. As new risks continue to be introduced to SaaS environments, security programs need to take an identity centric approach to brace what 2026 will bring.
SaaS security trends 2026 FAQs
What are the biggest SaaS security risks in 2026?
The biggest SaaS security risks in 2026 include data sprawl, employee-driven data exposure, non-human identities with excessive access, OAuth abuse, shadow AI usage, and supply chain risk from third-party integrations. These risks are amplified by limited visibility into how data moves across SaaS environments.
How is AI changing SaaS security?
AI is changing SaaS security by accelerating data creation, access, and movement across applications. AI tools often introduce new integrations, permissions, and configurations, increasing data exposure and configuration drift while making traditional security controls less effective.
Why is OAuth a growing SaaS security problem?
OAuth is a growing SaaS security problem because it enables persistent, token-based access that often bypasses traditional authentication controls. Attackers increasingly abuse OAuth grants to gain legitimate-looking access and move laterally across SaaS applications.
Why is insider threat a growing SaaS security risk in 2026?
Insider threat is a growing SaaS security risk because employees, former employees, and non-human identities have legitimate access to sensitive data. In SaaS environments, data can be copied, shared, or moved quickly, making misuse and accidental exposure harder to detect and prevent.
How can companies reduce SaaS data exposure?
Companies can reduce SaaS data exposure by improving visibility into sensitive data, enforcing consistent controls across SaaS applications, governing both human and non-human identities, monitoring integrations, and treating DLP as a coordinated program rather than a single tool.



